Understanding the Difference: Vulnerabilities vs. Vulnerability Exploitability eXchange (VEX)
In the world of cybersecurity, terms like "vulnerabilities" and "VEX" often get tossed around, but it's crucial to understand their specific meanings and implications.
Both play significant roles in the security posture of an organization but refer to very different concepts. Let's break down what each term means and how they differ from one another.

What Are Vulnerabilities?
In cybersecurity, a vulnerability is a weakness or flaw found in software or hardware that can be exploited by threat actors to gain unauthorized access or cause harm to data and systems.
Vulnerabilities can exist due to a variety of reasons, including, but not limited to, erroneous code, improper system configuration, or oversight in the software design. The impact of exploiting a vulnerability can range from minimal to catastrophic, potentially leading to data breaches, system downtimes, and compliance issues.
The identification, assessment, and remediation of vulnerabilities are critical tasks in the cybersecurity domain. These vulnerabilities are often identified through tools and processes like security audits, penetration testing, and the use of vulnerability scanners.
An Example of a Vulnerability Report
Below is an example of the well-known Log4Shell vulnerability discovered in 2021:
|
CVE Example: CVE-2021-44228 (Log4Shell Vulnerability) CVE ID: CVE-2021-44228 Date Published: December 10, 2021 CVSS Score: 10.0 (Critical) Description: The CVE-2021-44228 vulnerability, also known as Log4Shell, is a critical security flaw in the Apache Log4j 2 library, a popular Java-based logging utility used in many software applications and services. The vulnerability allows remote code execution (RCE) on the server or other computer running an affected version of Log4j 2. Affected Products: Apache Log4j 2 versions 2.0-beta9 to 2.14.1 Impact: Exploitation of this vulnerability can allow an attacker to execute arbitrary code on the server or other computer where Log4j 2 is used, potentially leading to full system compromise. Vulnerability Type: Remote Code Execution (RCE) CVE References: NVD - CVE-2021-44228, Apache Log4j Mitigation: Affected users should upgrade to Log4j 2.15.0 or later, as these versions contain fixes that prevent the exploitation of this vulnerability under default configurations. For environments where upgrading is not immediately possible, several mitigation strategies are recommended, such as removing the JndiLookup class from the classpath or setting specific Java system properties that disable the vulnerable code paths. |
As you can see, a vulnerability report shows which software is affected by a recently discovered vulnerability.
Sometimes, vulnerabilities go undiscovered for years or never!
What Is Vulnerability Exploitability eXchange (VEX)?
In contrast, Vulnerability Exploitability eXchange (VEX) documents are a relatively new concept introduced to provide transparency concerning the applicability of known vulnerabilities in the context of a specific environment, system, or component. A VEX document is a formal assertion by a software or hardware vendor regarding whether a product is affected by certain vulnerabilities identified elsewhere, such as in a National Vulnerability Database (NVD) or a Common Vulnerabilities and Exposures (CVE) list.
VEX is part of the broader Software Bill of Materials (SBOM) ecosystem, which is increasingly used in software development and IT asset management. The primary goal of VEX is to help organizations understand which components do not require mitigation actions against particular vulnerabilities because they are either not affected due to the configuration, feature non-use, or other factors that make the vulnerability non-exploitable in a given context.
The VEX Handling Process
The following diagram will focus on the process of creating and utilizing a VEX document. It explains how VEX documents assess the applicability of known vulnerabilities in specific products, helping organizations streamline their security efforts.
.png?width=6912&height=3456&name=CN-Assets%20(28).png)
Key Differences Between Vulnerabilities and VEX
In sum, a vulnerability is an actual flaw or weakness in a system. A VEX document, however, is a statement or disclosure about the exploitability of such vulnerabilities within specific products.
The identification of vulnerabilities aims to secure systems by patching flaws or implementing controls. In contrast, VEX documents aim to provide clarity and reduce unnecessary patching efforts where a vulnerability poses no real threat to the system due to its specific usage or configuration.
Vulnerability management processes involve scanning, detection, and remediation of security weaknesses. VEX documents are used in risk assessment processes to prioritize and refine these efforts based on the applicability of vulnerabilities to the products in use.
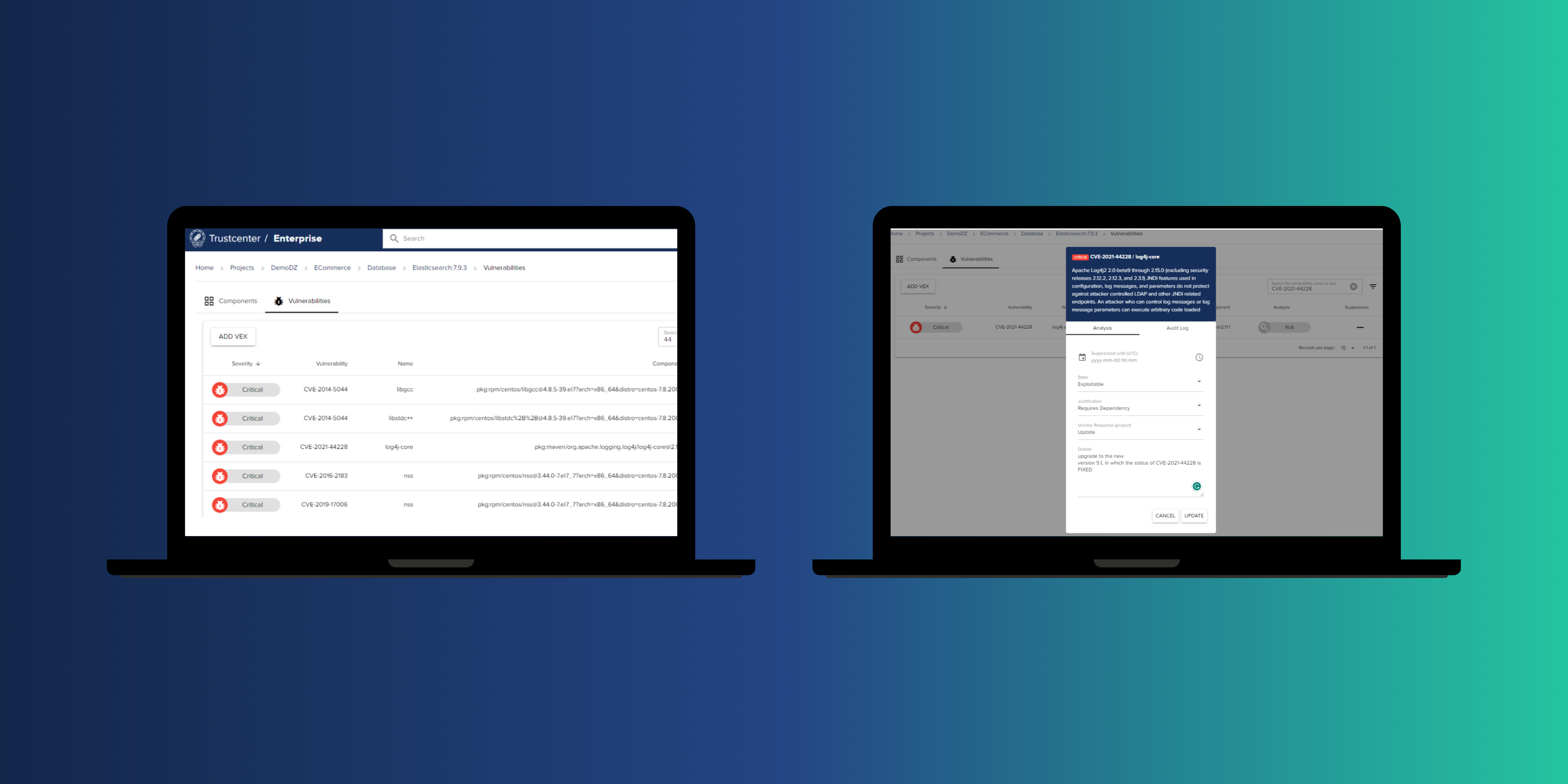
Good practices in software supply protection require one to keep a good eye on the known vulnerabilities and how they affect a software project. Many people nowadays use https://SBOM.sh to assess the vulnerabilities and risk score of a particular software repository, so that users can then draw up plans for mitigation.
In the screenshots below, you can see how an open-source project has been scanned by https://SBOM.sh for known vulnerabilities and then an overall risk score and is presented.
.png?width=6912&height=3456&name=CN-Assets%20(29).png)
.png?width=6912&height=3456&name=CN-Assets%20(30).png)
Link to the example SBOM dashboard
https://sbom.sh is free and used by over 100,000 software projects every single day.