Trustcenter / Enterprise
Total protection from bad and unwanted components for your application CI/CD pipelines.
AI-driven linting of applications, libraries, JAR files and repositories.
Real-time tracking of attestations and vendor risk profiles.
What our customers love about us
- Risk management:
Know in real time new threats arising from existing in-house developed and external applications. - Focus on real threats:
Filter out real threats by eliminating false positives. - SCA assessment:
Get a real-time risk score for your applications with reachability analysis. - Effective enforcement:
Bring discipline into your CI/CD to effectively exclude unknown or unsafe components.
- Application risk profile:
Create and maintain a software risk profile for compliance, audit, and regulatory adherence. - Real-time:
Continuously track attestation, application and stack risk profile. - Actions:
Point to actions to take to reduce the risk of vulnerabilities or exploits. - Integration:
Trustcenter integrates into dozens of DevOps platforms, monitoring tools, programming languages, and cloud infrastructure.
Identification and tracking of artifacts
World class SBOM management
Attestation management and distribution
Risk scoring for your apps
Compliance with cybersecurity regulations
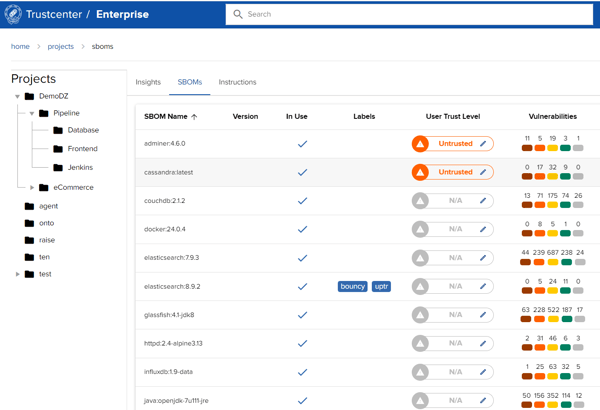
Secure the integrity of software supply chains and all the components used.
Import and export SBOMs from any format to any format. Generate detailed SBOMs for open source applications or containers. Analyze and gain new insights from your SBOMs.
Get a demo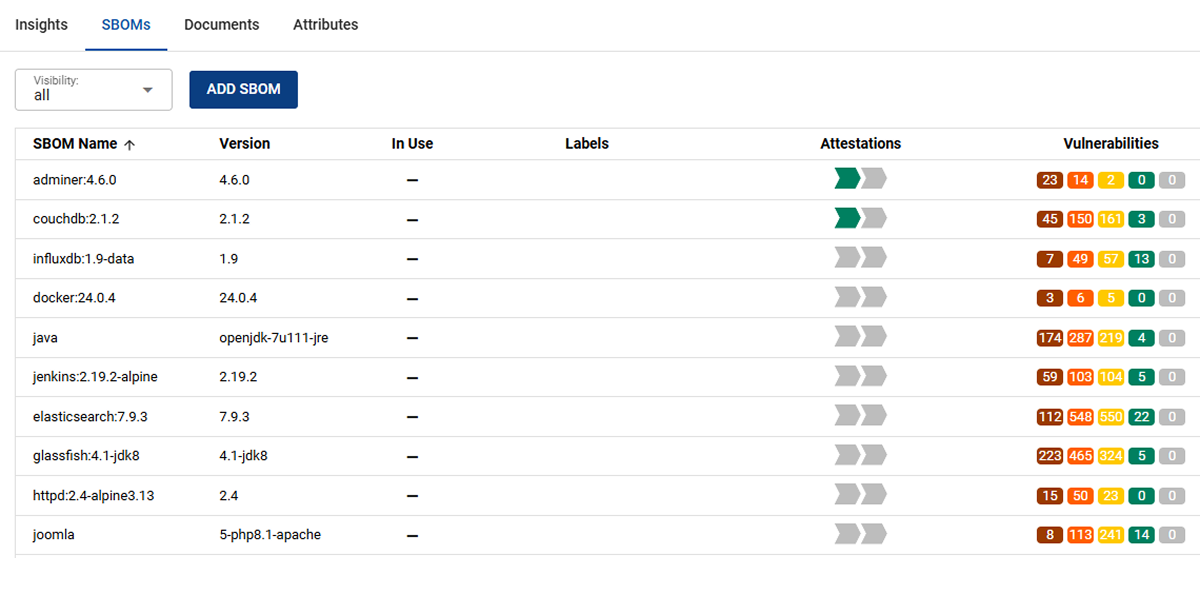
Only bake components into their applications that are known and trusted.
Unauthorized access to software repositories and build systems allows attackers to insert malicious code and components into software to be released. Trustcenter alerts you whenever unknown and/or trust components are detected!
Get a demo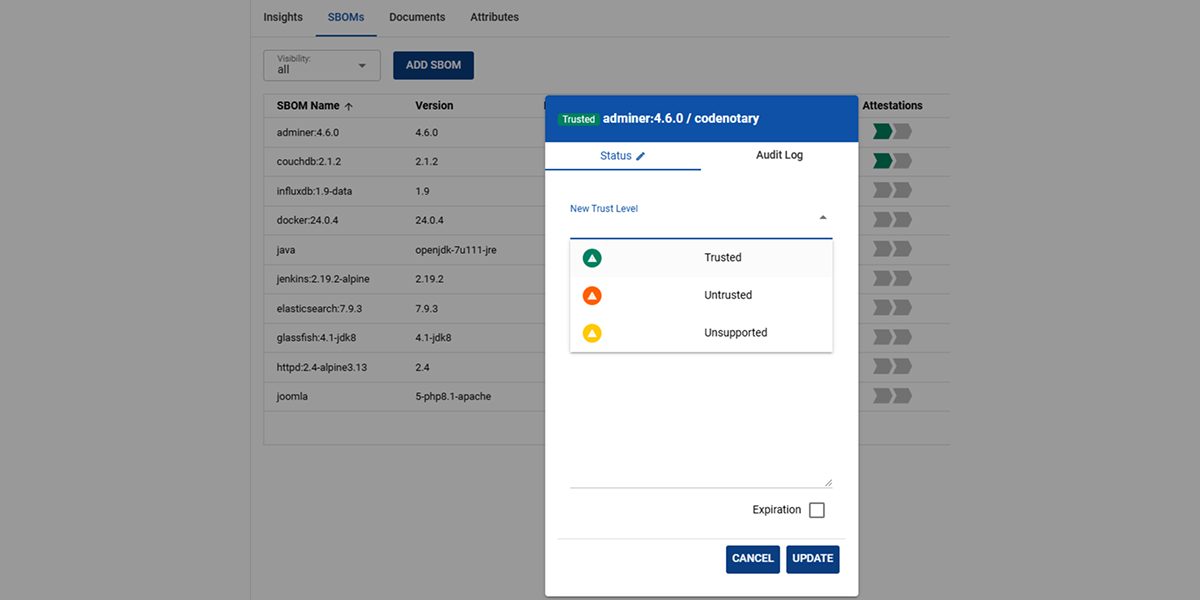
Trustcenter supports billions of artifacts!
Discover and catalog your workloads across all environments and track the state of all the components in your software projects and their dependencies.
Get a demo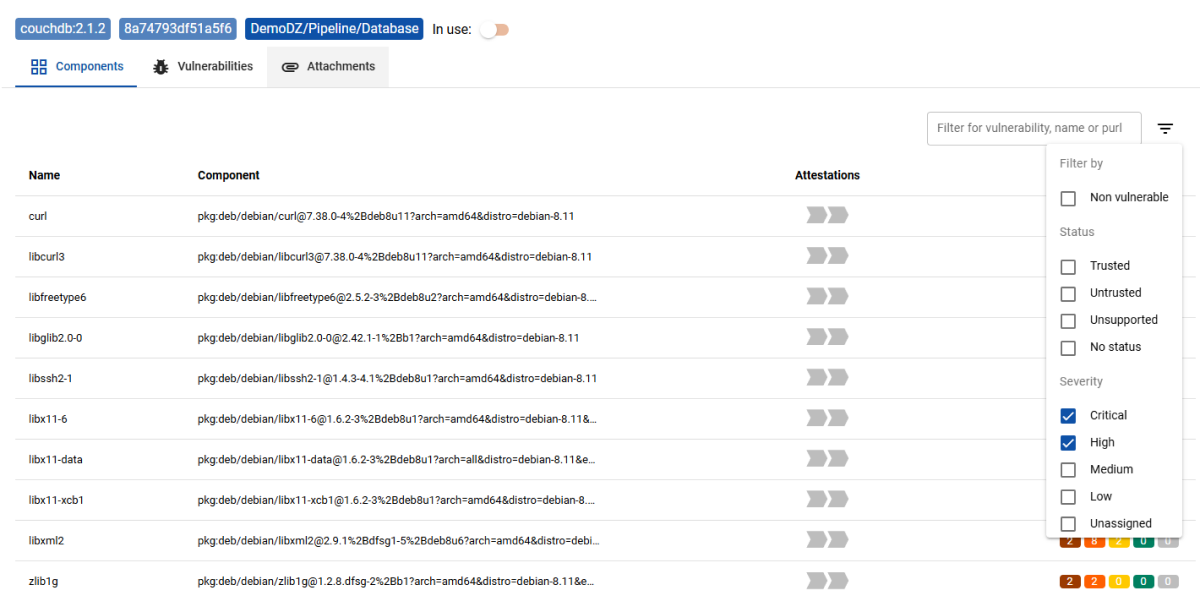
Re-evaluate all components continuously at rest and at runtime.
Enforce the deployment of container images built with known and trusted components.
Get a demo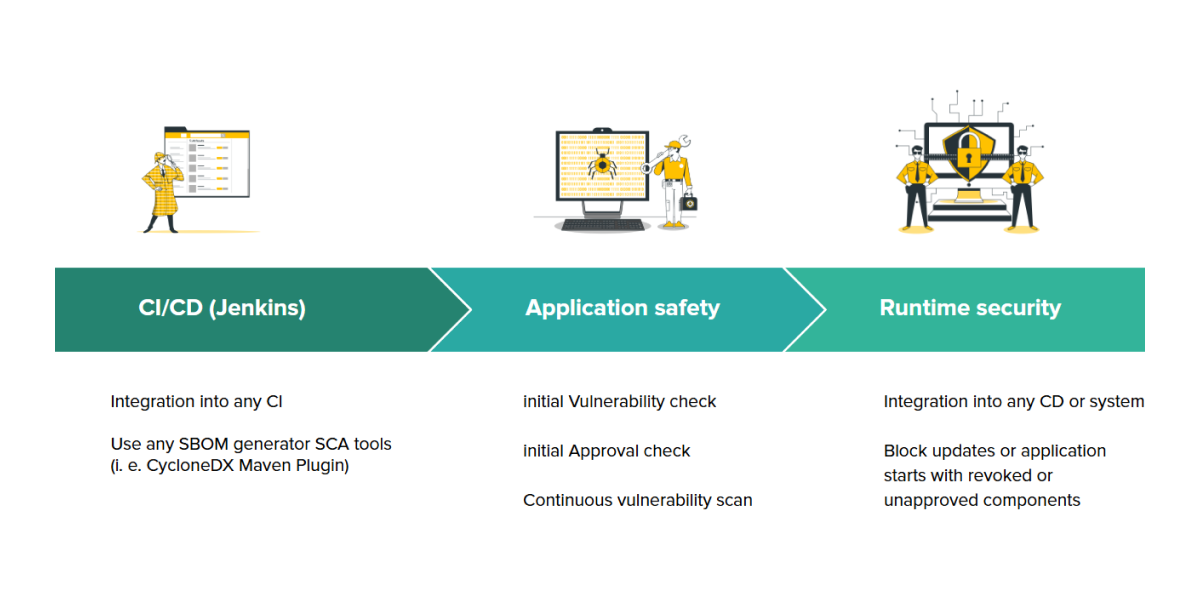
Know your components
Manage imported SBOMs from software vendors


Map your component journey
From CI/CD pipeline to apps to production
Monitor your software vendors risk profile
Track software license compliance
Monitor and track the dependencies of your app silos and establish cryptographic provenance for your artifact
Comply with artifact attestation guidelines like in-toto
Some of our integrations
CI/CD and SCM tools
Docker and OCI registries
Several vulnerability scanners (Snyk, Aqua, JFrog)
Bindings for Java, C++, Python, NodeJS, Go, Rust, PHP
Digital Signature platforms
Guardians of software™
Our mission is to deliver software supply chain protection and customer-specific business outcomes with a world class customer experience, leveraging the full capabilities of our applications.
