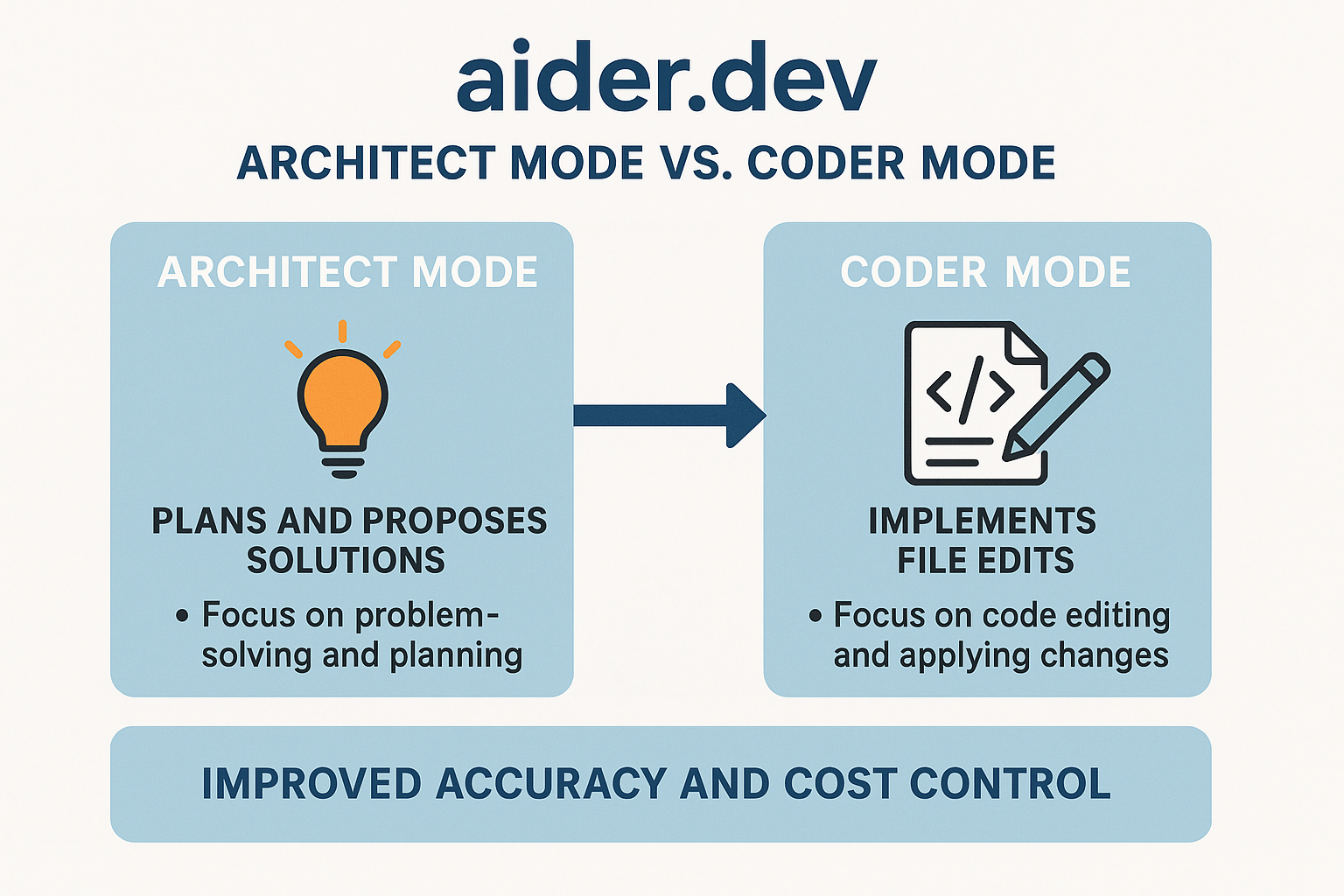
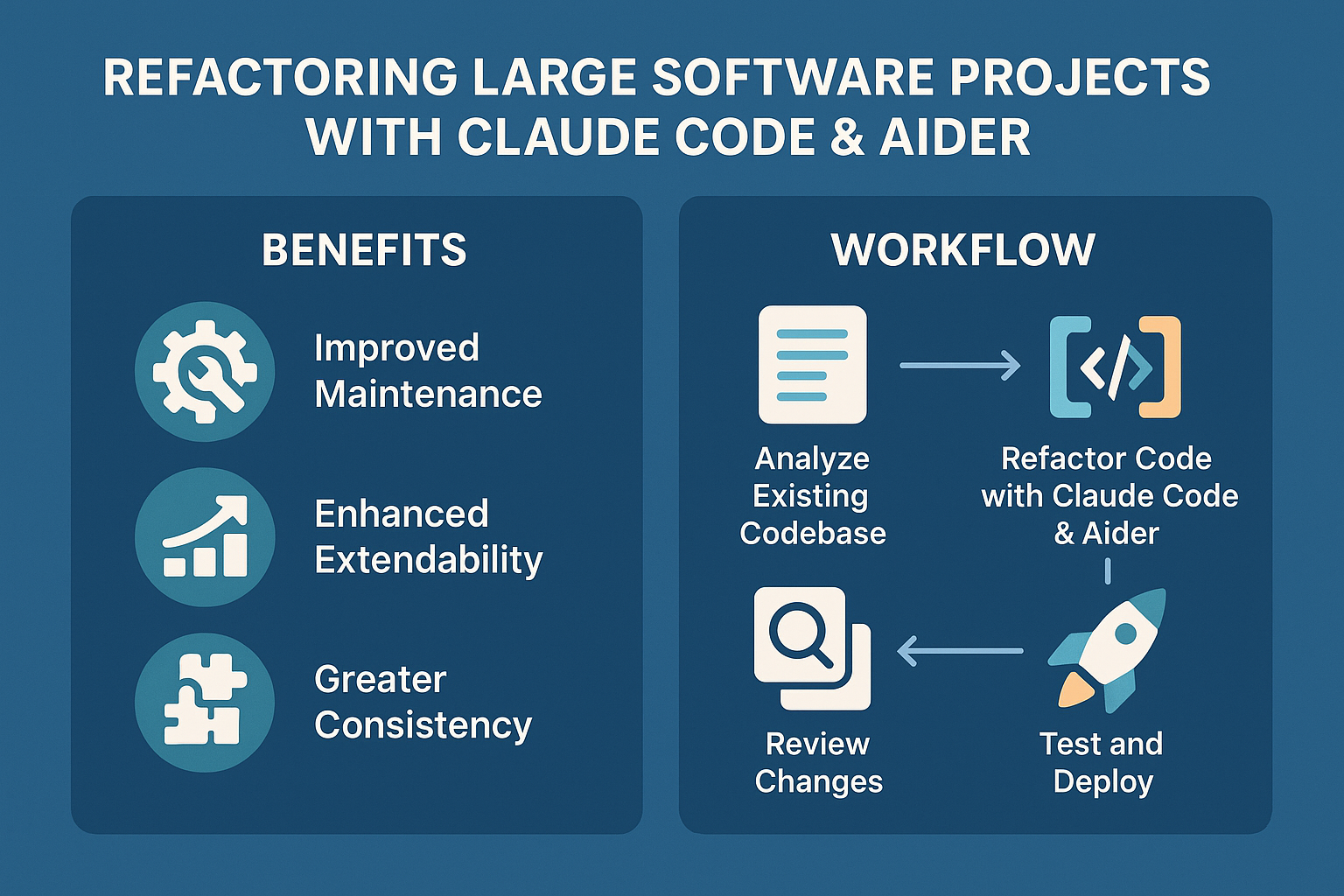
All you can read
Blog posts about Software Supply Chain Security, Software Bill of Materials, Code Signing, Trust enforcement, VDR, VEX and SLSA levels.
Posts by Tag
- Trustcenter (42)
- General (34)
- Metrics and Logs (29)
- SBOM (25)
- Vulnerability Management (18)
- AI (11)
- Data Security News (9)
- Linux (9)
- immudb Vault (9)
- SLSA (7)
- Security Tools (7)
- sbom.sh (7)
- Attacks and Breaches (6)
- CICD (6)
- Tips and Tricks (5)
- CycloneDX/SPDX (4)
- Provenance (4)
- Compliance (3)
- SSH (3)
- CISO (2)
- Cloud (2)
- DevSecOps (2)
- signature (2)
- API (1)
- Kubernetes (1)
- Product Updates (1)
Guardians of software™
Our mission is to protect the software supply chain using advanced AI technologies, while delivering customer-specific business outcomes through a world-class experience. We leverage the full capabilities of our applications to ensure our customers not only stay secure, but also achieve measurable value and resilience across their digital ecosystems.