Learn
A collection of articles to discover how Trust is protecting systems using AI
The EU Cyber Resilience Act and How Codenotary Enhances Compliance
The European Union's Cyber Resilience Act (CRA) is a landmark regulation aimed at strengthening cybersecurity measures across the EU. It mandates that manufacturers and developers of digital products ensure a high level of cybersecurity throughout a product’s lifecycle. The Act applies stringent security requirements to software, hardware, and services to mitigate risks and protect consumers and businesses alike.

Defending Apache Struts: Codenotary Guardian's Swift RCE Protection
Remote code execution vulnerabilities in Apache Struts typically arise due to insufficient input validation, deserialization flaws, or improper use of object-graph navigation language (OGNL). For instance, the infamous Struts 2 vulnerability (CVE-2017-5638) was caused by improper handling of untrusted user input, allowing attackers to execute arbitrary system commands via crafted HTTP requests.

Identifying and Neutralizing Attacks On your Linux Instances In 2025
Automated security tools such as firewalls, intrusion detection systems (IDS), and endpoint protection solutions play a crucial role in defending against cyber threats. However, sophisticated attackers continuously refine their techniques to evade these automated systems.
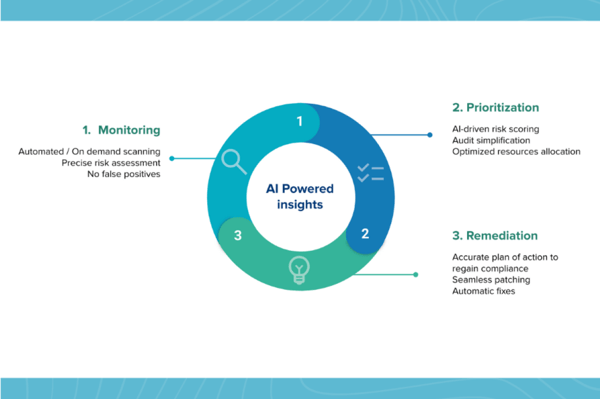
Vulnerability Management and Continuous Threat Exposure Monitoring
In today’s extremely rapidly evolving cybersecurity landscape, detection is a critical component of both vulnerability management (VM) and continuous threat exposure management (CTEM) programs. On some days, up to 200 new vulnerabilities are discovered for a typical Linux distribution.
Beyond Linux Updates: Holistic Security Remediation with Guardian AI
Keeping Linux systems up to date is a fundamental aspect of security best practice. Applying timely updates ensures that known vulnerabilities are patched, reducing the attack surface. However, updates alone are not enough. A comprehensive security strategy must also address other critical exposure points, such as open ports, non-standard-packaged applications, weak password policies, and compliance with cryptographic standards like FIPS-140.

Most dangerous Cyberattacks of the last 12 months
Cybersecurity threats in 2024 have been more sophisticated and damaging than ever. Major cyber attacks targeted corporations, governments, and individuals, often exploiting known vulnerabilities cataloged in the Common Vulnerabilities and Exposures (CVE) database. Let’s explore some of the most significant breaches and their connections to specific CVEs.
Enhancing Asset Monitoring: Why Guardian Outperforms Open-Source Tools
In today’s dynamic IT environments, organizations struggle with the continuous process of identifying, monitoring, and managing all internet-connected assets—both internal and external. This process is also known as Attack Surface Management or ASM. Every asset, from cloud instances and IoT devices to SaaS applications and third-party APIs, presents potential attack vectors that adversaries can exploit. Organizations need real-time visibility into these assets, continuous monitoring for exposures, and automated risk management. However, achieving this with traditional open-source tools is far from sufficient.
The U.S. Army's SBOM Mandate
The U.S. Army's recent Software Bill of Materials (SBOM) mandate marks a pivotal shift in military cybersecurity strategy, establishing a new standard for software supply chain transparency and security. Set to be fully operational by February 2025, this policy signals the growing recognition that in today's interconnected digital ecosystem, understanding what's inside your software is just as critical as securing your networks.
Guardian: Managing Linux Security from Your Windows Environment
As a Windows administrator suddenly tasked with managing Linux systems, you're probably looking for familiar tools - something with a clean web interface, clear reporting, and straightforward patch management. Let's talk about Guardian, a browser-based Linux vulnerability scanner that takes the mystery out of Linux security.
Securing Linux Systems: Why Vulnerability Scanning Matters
In March 2023, a Linux kernel vulnerability (CVE-2023-0461) allowed attackers to escalate privileges on thousands of systems before many teams even knew about it. By the time organizations started scanning and patching, some systems had been exposed for weeks. This isn't an isolated incident - it's a pattern that keeps repeating in Linux environments worldwide.
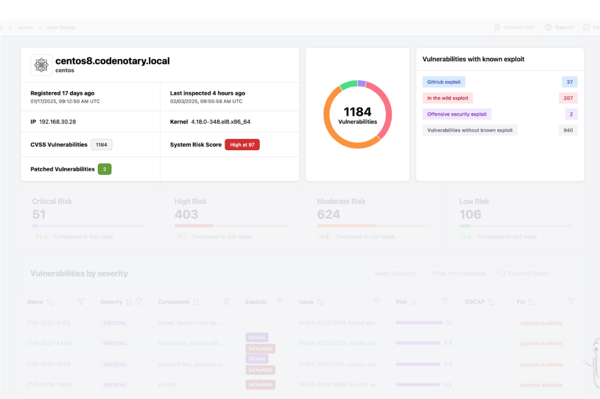
Beyond CVSS: Contextual Intelligence for Vulnerability Management
When a customer's CISO first said “we first check for highs and criticals, and when they’ll be fixed,” it sounded like a simple checklist—identify the high-risk vulnerabilities and patch them ASAP. However, as cloud workloads proliferated and our infrastructure became more complex, it quickly became clear that effective vulnerability management isn’t as straightforward as it appears.
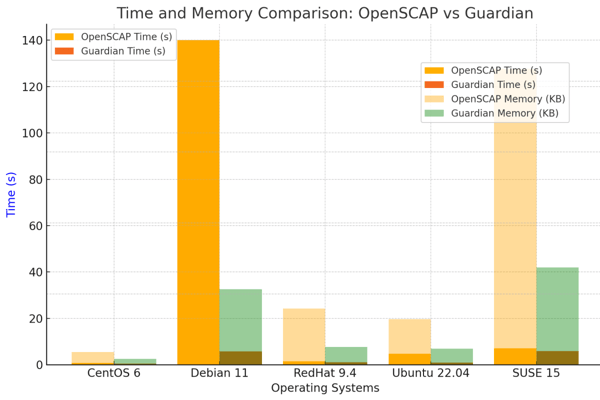
Guardian vs OpenSCAP: A Comparative Analysis
When it comes to ensuring the security and compliance of your systems, choosing the right tool can make a significant difference in both efficiency and resource usage. This blog post explores the benefits of using Codenotary's Guardian compared to OpenSCAP-based solutions, providing insights into their functionalities and performance.
Our mission is to secure the software supply chain with autonomous, agentic AI—delivering strong security outcomes through a platform that’s simple to use and requires no security expertise.