The U.S. Army's SBOM Mandate
The U.S. Army's recent Software Bill of Materials (SBOM) mandate marks a pivotal shift in military cybersecurity strategy, establishing a new standard for software supply chain transparency and security. Set to be fully operational by February 2025, this policy signals the growing recognition that in today's interconnected digital ecosystem, understanding what's inside your software is just as critical as securing your networks.
Understanding the Army's SBOM Mandate
The Assistant Secretary of the Army for Acquisition, Logistics, and Technology (ASA(ALT)) has issued a comprehensive policy requiring Software Bills of Materials for all covered computer software. This policy is a direct response to Executive Order 14028 on "Improving the Nation's Cybersecurity" and subsequent Office of Management and Budget (OMB) memoranda focusing on secure software development practices.
Key Highlights from the Army's SBOM Policy:
- Comprehensive Coverage: The policy applies to all programs currently executing or planning to execute on multiple acquisition pathways, including Software Acquisition, Urgent Capability Acquisition, Major Capability Acquisition, and Defense Business Systems.
- Mandatory SBOM Requirements: Program Executive Offices (PEOs) and Program Managers (PMs) must incorporate contract language requiring vendors to generate and deliver SBOMs for all covered computer software, including Government-off-the-Shelf, contractor-developed, commercial, and open-source software.
- Clear Implementation Timeline: Within 90 days after receiving guidance from the Deputy Assistant Secretary of the Army for Data, Engineering, and Software (DASA(DES)), PEOs and PMs must codify processes for SBOM collection, storage, management, and continuous monitoring.
- Continuous Risk Management: The policy emphasizes using SBOMs for ongoing vulnerability assessment, incident management, and supply chain risk mitigation throughout the software lifecycle.
- Collaborative Approach: A cross-PEO/PM SBOM Working Group will be established to facilitate knowledge exchange and promote collective problem-solving around SBOM implementation.
Why SBOMs Matter More Than Ever
The Army's move comes amid growing recognition that software supply chain attacks represent one of the most significant cybersecurity threats today. Modern applications typically contain hundreds or thousands of components, many of them open-source, creating a complex web of dependencies that can introduce vulnerabilities.
SBOMs provide a "nutrition label" or "ingredient list" for software, offering visibility into these components and enabling more effective vulnerability management. When a new vulnerability like Log4Shell emerges, organizations with comprehensive SBOMs can quickly identify affected systems and prioritize remediation efforts.
The Broader Impact
While the Army's policy directly affects defense contractors, it represents part of a broader government-wide push toward software transparency. Similar requirements are being implemented across federal agencies, and private sector organizations are increasingly adopting SBOMs as a best practice for cybersecurity and compliance.
This shift toward transparency aligns with the growing recognition that security through obscurity is no longer viable in today's threat landscape. Instead, organizations are embracing the principle that understanding what's in your software is fundamental to securing it.
Meeting the Challenge with Modern Tools
As organizations prepare to comply with these new requirements, specialized tools like Trustcenter/Enterprise and sbom.sh are becoming essential parts of the security toolkit.
How Trustcenter/Enterprise Supports SBOM Compliance
Trustcenter/Enterprise offers a comprehensive solution for organizations navigating the complexities of SBOM management. Its capabilities directly address key requirements in the Army's policy:
- Automated SBOM Generation: Trustcenter can automatically create standard-compliant SBOMs (in formats like SPDX and CycloneDX) during the build process, eliminating manual effort.
- Centralized SBOM Storage: The platform provides secure, centralized storage for SBOMs, meeting the Army's requirement for PEOs/PMs to "securely store and manage SBOMs."
- Continuous Monitoring: Trustcenter's continuous monitoring capabilities allow organizations to track vulnerabilities across their software supply chain in real-time, supporting the Army's emphasis on "continuous monitoring of SBOMs."
- Immutable Audit Trail: Using immutable ledger technology, Trustcenter maintains a tamper-proof record of all software components, providing verifiable evidence of compliance.

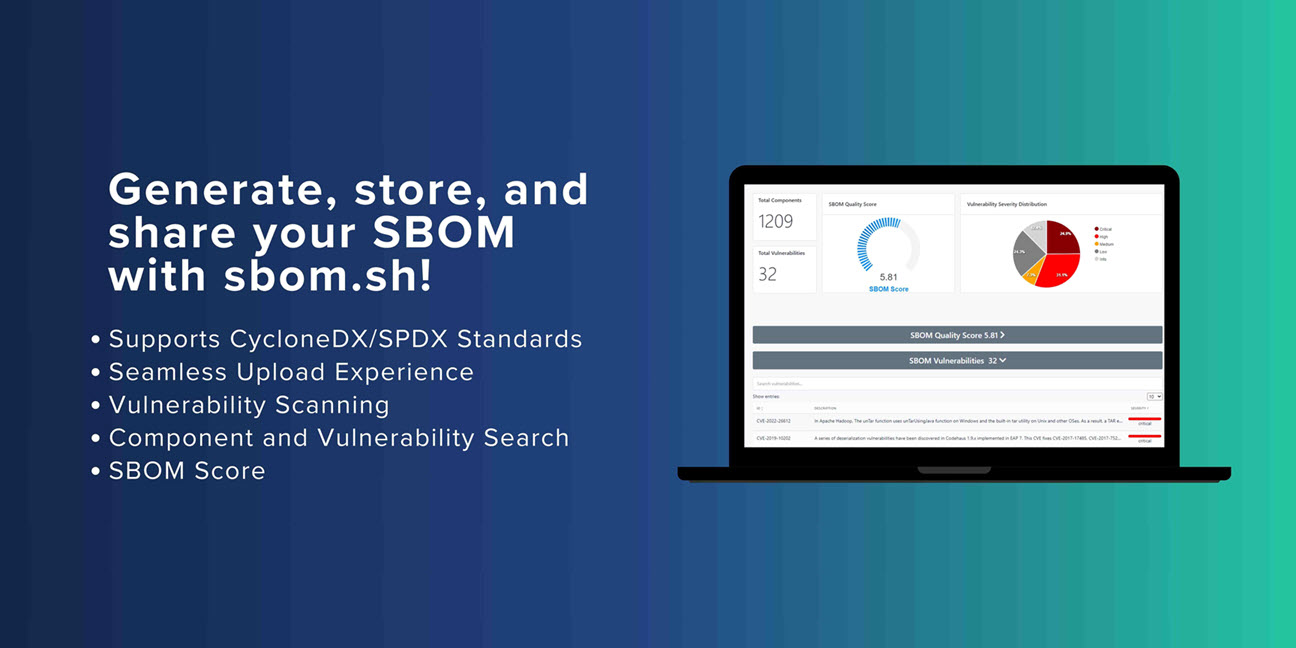
The Role of sbom.sh
For organizations looking for a lightweight, flexible solution, https://sbom.sh offers a free and easy entry level solution for SBOM generation and management:
- Rapid SBOM Creation: sbom.sh can quickly generate SBOMs for various types of software projects, helping contractors meet delivery requirements.
- Format Flexibility: Supporting multiple SBOM formats, sbom.sh ensures compatibility with different systems and requirements.
- Integration Capabilities: Easy integration with CI/CD pipelines allows for automated SBOM generation as part of the software delivery process.
- Accessibility: As an open-source tool, sbom.sh provides a low-barrier entry point for organizations beginning their SBOM journey.
Preparing for the Future
As the February 2025 deadline approaches, defense contractors and software vendors should be taking concrete steps to prepare:
- Inventory Current Software: Begin by understanding what software you're currently delivering to the Army.
- Assess SBOM Capabilities: Evaluate your current ability to generate, manage, and analyze SBOMs.
- Select Appropriate Tools: Based on your needs, implement solutions like Codenotary Trustcenter Enterprise or sbom.sh.
- Develop Processes: Create clear workflows for SBOM generation, delivery, and vulnerability management.
- Train Personnel: Ensure your team understands SBOM concepts and implementation requirements.
Conclusion
The Army's SBOM mandate represents more than just a new compliance requirement—it signals a fundamental shift in how organizations approach software security. By embracing transparency and adopting tools like Codenotary Trustcenter Enterprise and sbom.sh, defense contractors can not only meet these new requirements but build more resilient software supply chains in the process.
In an era where software vulnerabilities can have strategic implications for national security, the Army's focus on SBOMs demonstrates a proactive approach to addressing the complex challenges of modern cybersecurity. For software vendors and defense contractors, adapting to this new paradigm isn't just about compliance—it's about contributing to a more secure digital ecosystem for all.