Detect unwanted dependencies in your software like versions of faker.js or colors.js
Last weekend the Open Source world was shaken up a bit when a developer maintaining the highly popular libraries faker.js and colors.js sabotaged both projects by breaking their function.
The supply-chain dangers from underlying open-source projects were highlighted many times in 2021, the year that ended with the Log4j disaster. But as the new year shows, it’s not just about vulnerabilities, it’s about detecting any kind of dependencies to mitigate risk if something unwanted happens to them.
This blog doesn’t comment on the reasoning of the developer and focuses on a bigger problem:
How can a developer, project manager, DevOps engineer or CISO make sure that important applications are not affected by a certain version of a dependency!
Most tools out there focus on vulnerabilities and malicious code inside applications and dependencies, but this kind of “attack” is more subtle. As a developer or application maintainer, I just want to make sure not to use a certain library or a certain version in my code.
Quick wrap up of what happened to faker and colors
A developer inserted code into two very popular open-source npm software libraries and published it on the npm package repository. The code added generated a string of characters into applications that use those libraries. The libraries are not just less-known pet projects but highly popular ones used by thousands of projects and are downloaded millions of times a week. You can read more here: Bleeping Computer
What does remediation look like?
- Projects and software using the affected versions of colors and faker were forced to revert to older versions (and find out what version to use first) to fix their apps. (currently Colors.js 1.40 and Faker.js 5.5.3)
- Stop new build pipelines using the affected libraries and change the code accordingly before resuming the pipelines
- Stop using the affected version of the popular Amazon AWS’s Cloud Development Kit
The bigger issue
Despite the trouble making sure all applications are back to normal, there is a bigger issue at hand. The same scenario can happen to any Open Source library out there and instead of breaking the functions immediately, it could start at a certain time in the future, when the library is already pushed to production. Also, the Open Source license could change, or … so many other unwanted things can happen.
The only real solution here is to be on top of the dependency usage and deployment. Software Bill of Materials (SBOMs) can be a solution to that issue, but they need to be tamperproof, queryable in a fast and scalable manner, and versioned.
Codenotary Cloud and the tamper-proof, queryable dependency
Using Codenotary Cloud and the vcn command-line tool, you can send all artifacts including their SBOM (dependency list) to an immutable data structure and give it a trust level in a tamperproof and auditable way.
Notarize your artifacts including SBOM: vcn notarize –bom dir://folder or vcn notarize –bom docker://image
That is typically automated in your CI/CD pipeline or using Github actions, so you eventually have a full catalog of everything and are always up to date.
At any point in time, you can simply search by a name or a checksum to know where and when your artifact or dependency is used:
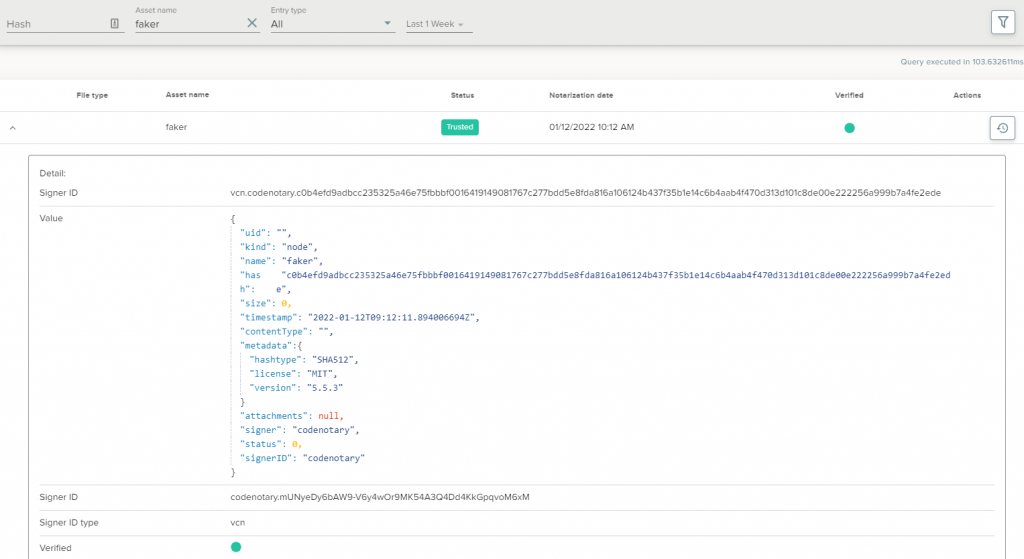
Summary
Software is never complete and the code base including its dependencies is an always updating document. That automatically means you need to track it, good and bad, keeping in mind that something good can turn bad.
And the downside of simply trusting project maintainers or digitally signed builds is getting more obvious every day. Therefore, maintaining the integrity of software supply chains will be an ongoing problem for users and vendors for the years to come.