using-blockchain-to-protect-against-wire-fraud-scams

2018 witnessed a near doubling of the amount of money lost to cybercriminals at an alarming $2.7 billion according to the latest FBI Internet Crime Report. The figure takes into account various types of internet fraud, including those that utilize irreversible wire transfers, which attackers love. In our previous blog in the series here, we talked about invoice fraud. This blog discusses the liability companies and individuals bare when attacks happen, various different tactics hackers use to achieve fraudulent wire transfers, best practices for data security, and how to mitigate the risk and fallout of an attack using blockchain.
Liability
Liability is part and parcel with doing business. In the real estate industry, no professional is absolved from the liability of a data breach. If you are in possession of a client’s sensitive data and it’s stolen, both you and your company are liable. This applies to agents, lawyers, brokers, and anyone else who is even a temporary custodian of a client’s sensitive information, regardless if they are actually initiating fund transfers or not.
For example, in the real estate industry, one of the biggest claims made against agents today is due to client data compromise. Across industries, data breaches directly cost businesses an average of $3,000,000. However, that figure doesn’t include the $1,300,000 average cost of lost business that happens in the wake of compromise, which brings the grand total to businesses to $4,300,000 per compromise.
Overview of Attack Types
Hackers use a variety of ways that lead to their ability to carry out wire fraud. To steal social security numbers, names and addresses, bank account numbers, pin codes, and other financial information, hackers combine tactics such as:
- Malware: software used to gain access to legitimate computer or communication systems e.g. email threads containing financially relevant data. The hacker uses the information to mask themselves from security detection efforts when they execute fraudulent wire transfer requests.
- Spear-phishing: Emails from a bad actor impersonating a trusted sender used to entice victims into revealing confidential information.
- Spoofing email accounts and websites: Legitimate addresses with slight variations in them that are used to fool victims into thinking fake accounts are authentic. For example, adam.kelly@commerce.com vs adam.keIIy@commerce.com, which look virtually identical because of the swap between the lower-case l’s and the capital I’s.
The Role of Social Engineering
In addition to the above-listed tactics, hackers employ what’s known as social engineering. It attacks the human element of security. Specifically, social engineering refers to the use of deceptive techniques to manipulate a person into breaking standard security practices and disclosing personal or confidential information. And it doesn’t matter how much money or resources a company threw at securing their network, the human element is a large and constant vulnerability for hackers to exploit. Security protocols can help protect a company. However, there is always the human element to consider.
Here’s a good, 2.5-minute video from DefCon on just how easy social engineering is. It shows a social engineer gaining access to the interviewer’s phone account, adding her name to his account, and changing his password within just a few minutes using nothing more than a YouTube video of a crying baby and some wit. This type of attack can blast right through the most state-of-the-art security.
That said, it is still wise to implement security measures data protection.
Data Security Best Practices
There are numerous best practices organizations can employ to help protect against data compromise. Here is a list of several:
- Always follow up an email containing wire instructions with a phone call before sending any funds.
- Create a data retention policy and delete or destroy all out of date documents.
- Establish an electronic records management system.
- Continuously create data backups so nothing is lost in the event of compromise.
- Use file integrity software to ensure assets are not unknowingly changed while at rest.
- Enforce a policy to restrict access to sensitive data to only approved devices and personnel.
- Keep antivirus, firewall, and all other security software up to date with the latest versions and perform software reviews on a quarterly or biannual basis.
Preventing Fraud with Blockchain
Codenotary is a platform that ensures the integrity of clean, trusted software-based assets that are in use or at rest. By independently notarizing and attaching their identity and trust to any digital asset, individuals and organizations can ensure their integrity. The intelligence that Codenotary delivers is based on a combination of blockchain technology and Know Your Customer practices. This way team members, stakeholders, and consumers can know if an asset is trusted, who testified to its trustworthiness and how they have proven who they are. In short, Codenotary transforms trust from an implicit assumption to an explicit authentication for anyone, anywhere, at any time.
How Codenotary Works
Codenotary works on a simple premise. If the digital fingerprints of two compared files match, trust is authenticated. One fingerprint is of the digital asset that is being authenticated, while the other belongs to a known safe version of the file that was previously recorded to the blockchain. This way stakeholders and corporations can always authenticate their files containing sensitive financial information and wire instructions have not been changed maliciously or by an unauthorized user, even in the aftermath of compromise.
See Codenotary’s Authentication in Action
In two quick steps, you can witness Codenotary in action.
-
Download this popular app, AutoHotKey (3.5 MB), from the publisher’s website. (You don’t need to open the file. Just download it.)
Current version: v1.1.30.03 – April 5, 2019 (https://www.autohotkey.com/download/)
- Drag and drop the AutoHotKey file on to Codenotary’s Authenticate page here.
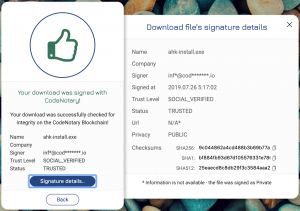
As soon as you do you will see the ‘thumbs up’ icon, file hashes, and associated blockchain stored metadata for the file letting you know it is safe to use.
REFERENCES:
https://www.hanover.com/articles/wire-scam-affecting-lawyers.html
https://www.cresinsurance.com/document-management-tips-avoid-costly-real-estate-lawsuits/
https://www.fbi.gov/news/pressrel/press-releases/fbi-releases-the-internet-crime-complaint-center-2018-internet-crime-report
https://pdf.ic3.gov/2018_IC3Report.pdf
https://www.youtube.com/watch?v=lc7scxvKQOo
https://www.timberlandbank.com/resources/security-center/wire-transfer-scams
https://www.cnbc.com/2019/04/09/new-wire-fraud-scam-targets-your-direct-deposit-info-paycheck.html
