The rise of supply chain attacks
Supply chain attacks are on the rise. Why are they so attractive to cybercriminals? The reason is simple. Most of the industry is not yet ready to efficiently defend against them and once successfully deployed the chances of having a big impact are high. Tampering with the software supply chain of SolarWinds affected 18,000 customers. Even more widespread was the log4j exploit with a huge number of servers affected and a targeting rate of 50%. Political activism also discovered the huge impact of supply chain attacks as seen in a famous npm package that was modified by its own developers to spread their message and delete files. The biggest challenges of securing the software supply chain come from:
- Open-Source Software
- Vendor supplied Software
- Insider Threats
For open-source software, it’s become really clear that we have to know what’s inside. Therefore the concept of SBOMs (Software Bill of Materials) will be mandatory in the near future. Operations of every IT company have to be enabled to quickly answer the following questions: what is running on my systems and where does it come from? Those question don’t sound very complicated but in reality, it is a nightmare to identify software in a complex environment and trace it. Code signing is an important concept to simplify that process. The idea is to sign every software artifact that comes from you therefore making it possible to instantly identify what is yours and what isn’t (also known as provenance checks). Codenotary offers code signing using a zero-trust architecture. It can also create SBOMs in any language and container.
Vendor supplied software remains difficult to handle. Vendors should supply SBOMs in the future to comply with the cybersecurity act of president Biden. Vendors will also benefit from that, given they don’t have to worry about panicked customers asking them if they are affected by a vulnerability. With Codenotary it is possible to attach the SBOMs to the signed software without having to worry about the SBOMs being lost or tampered.
One mostly overlooked threat is the insider attack. Large IT organizations have thousands of contractors and employees who represent a cross-section of society. They can make mistakes or even act outright maliciously. The example of the node developer from above who changed his code to spread a political message is just one possible scenario. Codenotary is built on a zero-trust architecture. It uses immudb, an open source tamper-evident database. Attackers are not able to cover up their tracks.
Conclusion
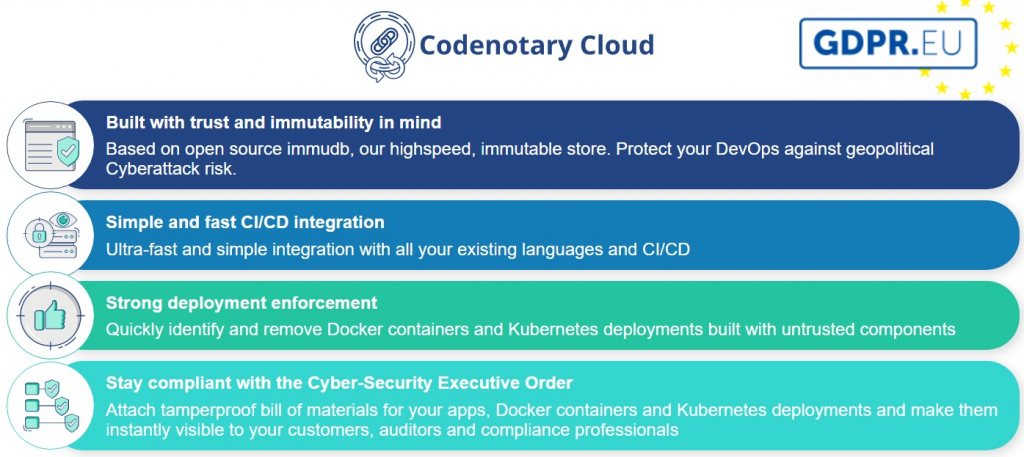
Supply chain attacks and vulnerabilities are already there. Most of the businesses in the industry have been already affected. Exploits like log4j will pop up again and again. Therefore it is important to quickly identify and remove unwanted software to not get targeted by cyber attacks. Codenotary Cloud is offers an all-in-one solution for a secure software supply chain. It complies with the cyber security executive order and feature a zero-trust model by the use of Codenotary’s immudb. Codenotary Cloud can be integrated easily not only in Cloud environments but also in legacy platforms.
