Serious security vulnerabilities in Atlassian Confluence affect many organizations
Last weekend was all about releasing fixes for a major (critical) Confluence server vulnerability, tracked by CVE-2022-26134, that allows an unauthenticated attacker to execute arbitrary code (remote code execution, RCE).
You should be very aware of that vulnerability as Confluence servers are a very attractive target for initial access to a corporate network. Therefore, systems should be updated immediately, mitigated, or taken offline. Not doing so will ultimately lead to significant attacks, including devastating ransomware deployment and data theft.
Atlassian recommends to ban external access to affected Confluence servers!
Affected versions of Confluence Server and Data Center, are from 1.3.0 before 7.4.17, from 7.13.0 before 7.13.7, from 7.14.0 before 7.14.3, from 7.15.0 before 7.15.2, from 7.16.0 before 7.16.4, from 7.17.0 before 7.17.4, and from 7.18.0 before 7.18.1.
You can also find more information about the vulnerability here:
https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
Exploits are publicly released
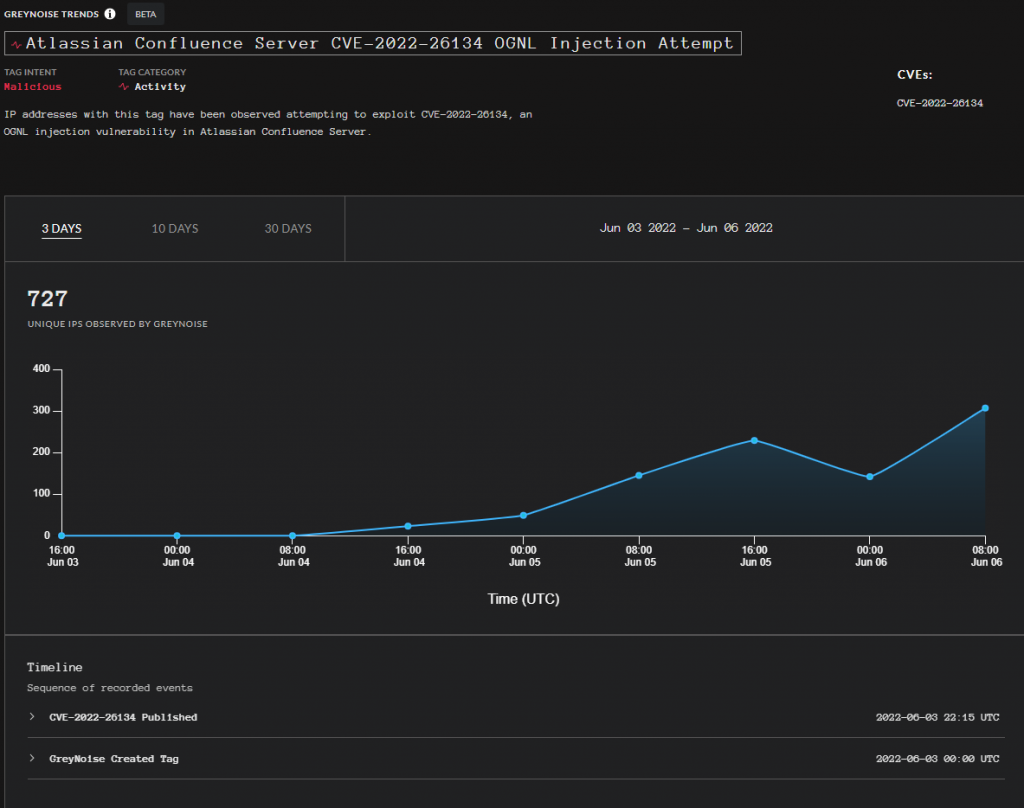
Starting June 4th the first injection attempts were tracked and they are on the rise.
How does the injection work
The vulnerability is an Object-Graph Navigation Language (OGNL) injection, where a threat actor places a malicious payload in the URI of an HTTP request. Any request (not just GET), even invalid ones can be used.
When the server receives the request it processes it and performs a translateVariables method. Using a certain expression causes the method to forward parts of the payload to a findValue method that executes the code. There are more methods that can be used for the exploit.
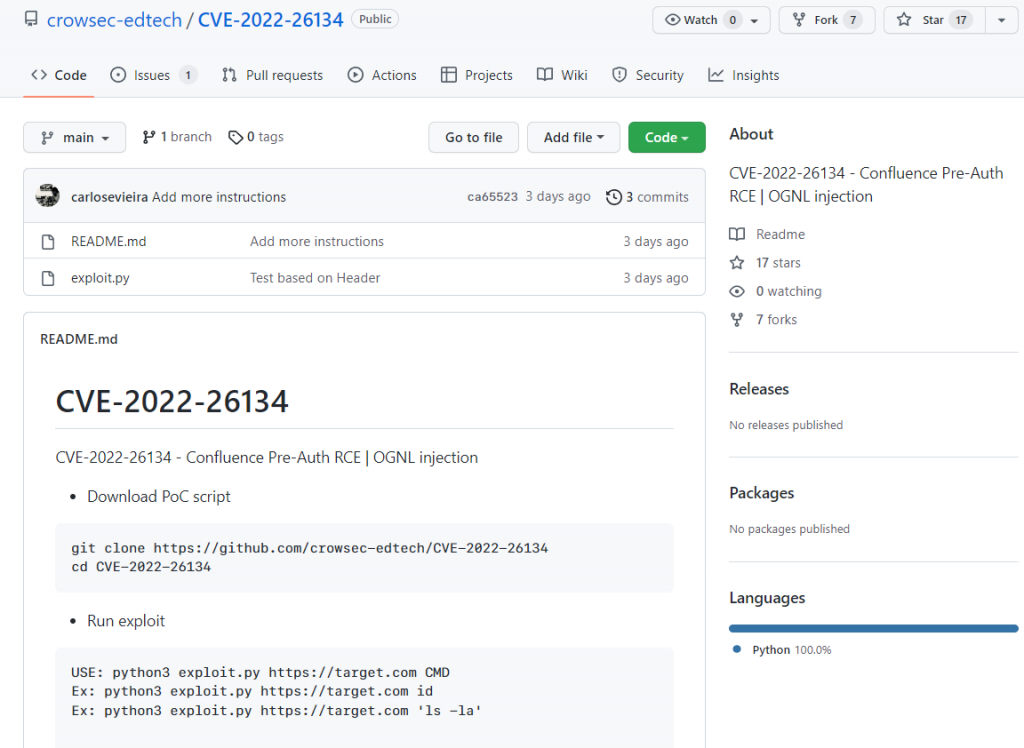
There is a Python PoC example of the exploit that is already being used by good and bad people.
Patch your Confluence servers
In case you haven’t patched the security vulnerability in your Confluence or Data Center servers, you should act now as exploits are already happening.
“Released versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1 which contain a fix for this issue,” explains the Atlassian advisory.
If for some reason, you are unable to patch your servers immediately, Atlassian has provided mitigations for Confluence 7.0.0 through version 7.18.0. https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
