Rust-based Ransomware can hit anywhere including Windows, Linux and VMware ESXi
While it’s great for application developers to write applications in a language that runs seamlessly on many different operating systems, there is a downside to the application’s intention. Ransomware has damaged many companies, causing downtime, money, and sleepless nights. Looking into some statistics you can find damage predictions of $265 billion by 2031.
Writing Ransomware software in a development language like Rust opens new ways of attack as it can be easily compiled to work on many different operating systems including hypervisors like VMware ESXi.
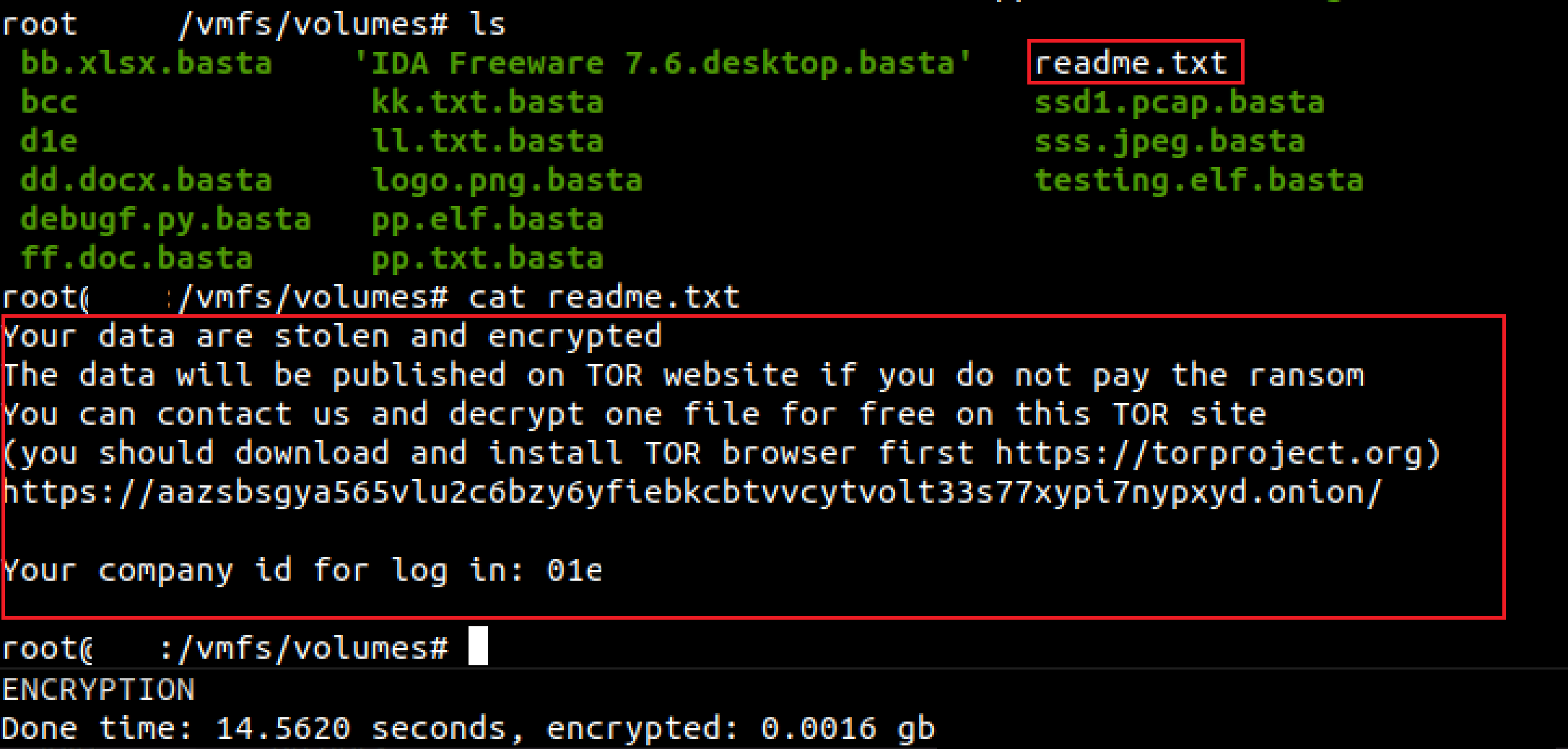
There is a syndicate called Black Basta that provides ransomware-as-a-service (Raas) that became prominent very quickly by amassing 50 victims within 2 months and is known for cross-platform ransomware development. And that cross-platform ransomware is already becoming a trend.
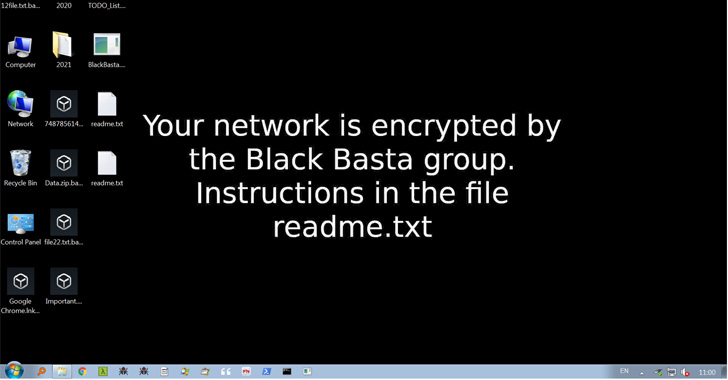
Some researchers warn that “Ransomware remains a big problem for today’s society – as soon as some families come off the stage, others take their place.” It is becoming the biggest global cyber treat.
To avoid being the next victim on the list many countermeasures are required and will help guard against many new problems that will arise over the coming months and year. Here are some general guidelines.
Know your software
An important countermeasure is to have a actively maintained catalog of the software that is running in your data center, computer, and edge device. Having SBOMs (Software Bill of Materials) and active search capabilities over dynamic SBOMs is a great help. Especially for cross-platform ransomware which typically is delivered as a single binary and the unique checksum disclosed by ransomware researcher or as part of security advisories.
As an example, one version of the ransomware binary hash (or checksum) that can affect Linux and VMware ESXi is 0d6c3de5aebbbe85939d7588150edf7b7bdc712fceb6a83d79e65b6f79bfc2ef.
Having a software platform like Codenotary Trustcenter enables you to simply search for this checksum or any other you are aware of. That way you can find out if you already have that component in your environment or get alerts the moment it is detected somewhere. Of course you can also pro-actively untrust these hashes when you read about it, so your build and/or deployment process don’t even continue when such a checksum appears.
Be aware
The chances of becoming a victim of a ransomware attack are increasing every day. The bad actors are very creative with email campaigns, social engineering or even fake job offers. Having Web Application Firewalls (WAF) in place is very important to protect against exposed software and database vulnerabilities. Antivirus software and vulnerability scanner to detect known threats. Backup and Archiving solutions need to be in place as well – the last resort.
But awareness of every team member in your company or organization is of huge importance.
- Double-check if the tone of the email isn’t weird coming from someone you know
- The attachment looks weird or are uncommon, i. e. xls instead of pdf
- Why does someone reach out to update my Google business address
- Why do I get a credit note from a company I didn’t order anything for a long time
There is much more to it, but in general – if something looks fishy, don’t open it.
Software Updates
Updating software and operating systems is always a bit risky, but not updating it is even riskier today. If there is an exploit that can be used because of an older version of a library or application, you open the doors for malicious code including ransomware. Log4j is still a very present example and will take a long time before the exploit will stop and the updates are in place.
Permissions, Permissions, Permissions
Many applications can’t do much or limit damage when the permissions are restrictive. The principle of least privilege is key and very important. Don’t open applications with elevated permissions you don’t know and are scanned and approved. Don’t log in as root or use sudo to run applications.
