Making the Most of Dependency Graphs for Softwares
When it comes to software development, managing dependencies helps ensure that it's all smooth, secure sailing. GitHub's Dependency Graph is a powerful tool designed to help identify and manage dependencies in an easy-to-understand manner. The graph also empowers you to generate and download a Software Bill of Materials (SBOM) in SPDX format via the GitHub API.
However, the generated SBOM may lack some crucial details like quality, vulnerabilities, or exploitability. This is where sbom.sh comes to the rescue, offering a comprehensive solution to enrich your SBOM.
In this article, we'll break down how all of this works.
.jpg?width=1200&height=630&name=Extract%2c%20track%2c%20and%20enforce%20software%20components%20(1).jpg)
What is the Dependency Graph?
In one sentence: The Dependency Graph is a summary of the manifest and lock files stored in a GitHub repository.
These files contain information about the dependencies your project relies on. Additionally, the graph includes any dependencies submitted using the Dependency submission API. For each repository, the Dependency Graph reveals:
- Dependencies: The ecosystems and packages your project depends on.
- Dependents: The repositories and packages that depend on your project.
Using the graph is straightforward. When you push a commit to GitHub that modifies or adds a supported manifest or lock file to the default branch, the Dependency Graph is automatically updated. This update also occurs when changes are made to the repository of one of your dependencies.
The graph provides valuable insights, such as license information and vulnerability severity for each dependency. You can even search for specific dependencies using the search bar. It also helps in organizing dependencies by sorting them based on vulnerability severity.
Leveraging the GitHub API
To generate an SPDX-formatted SBOM using the GitHub API, you need to follow a few steps. The bearer token, acting as your identification, is essential for this process. This token is associated with your GitHub profile's developer settings.
Here's how to obtain your bearer token:
-
Visit Your GitHub Developer Settings: Go to your GitHub account, navigate to "Settings," and find the "Developer settings" section.
-
Access Personal Access Tokens: Within "Developer settings," click on "Personal access tokens." Generate a new token with the required scopes for SBOM generation.
-
Copy Your Bearer Token: Once generated, copy the token. Treat it with care, as it serves as your authentication to access GitHub data.
Supported Package Ecosystems
GitHub's Dependency Graph supports a variety of popular package ecosystems, each with its recommended formats. These ecosystems include:
- Cargo (Rust)
- Composer (PHP)
- NuGet (.NET languages, C++, etc.)
- GitHub Actions workflows (YAML)
- Go modules (Go)
- Maven (Java, Scala)
- npm (JavaScript)
- pip (Python)
- pnpm (JavaScript)
- pub (Dart)
- Python Poetry (Python)
- RubyGems (Ruby)
- Swift Package Manager (Swift)
- Yarn (JavaScript)
Using these recommended formats ensures the accuracy of your dependency graph, reflecting the current build setup and reporting vulnerabilities in both direct and indirect dependencies.
Enriching Your SBOM with sbom.sh
The Dependency Graph offers practical uses, allowing you to:
- Explore the repositories your code depends on and those that depend on it.
- View and update vulnerable dependencies for your repository.
- Get information about vulnerable dependencies in pull requests.
While the GitHub API provides a basic SBOM, sbom.sh takes it up a notch by enhancing the information. It not only adds quality metrics but also provides insights into vulnerabilities and exploitability. It also helps that it's easy as 1, 2, 3.
-
Visit sbom.sh: Head to sbom.sh and navigate to the "GitHub SBOM" section.
-
Authorize with GitHub: Click on the "Authorize with GitHub" button. This step allows sbom.sh to access the necessary data.
-
Paste Your Bearer Token: You'll be prompted to provide your GitHub bearer token. Paste the token you obtained from your GitHub developer settings.
-
Generate and Share: Once authorized, generate your enhanced SBOM. The resulting SBOM includes not only the basic SPDX information but also detailed insights into the quality, vulnerabilities, and exploitability of your project's dependencies.
The enriched SBOM obtained from sbom.sh is a powerful resource. You can share this detailed information with team members, collaborators, or stakeholders, providing a comprehensive overview of your project's dependencies.
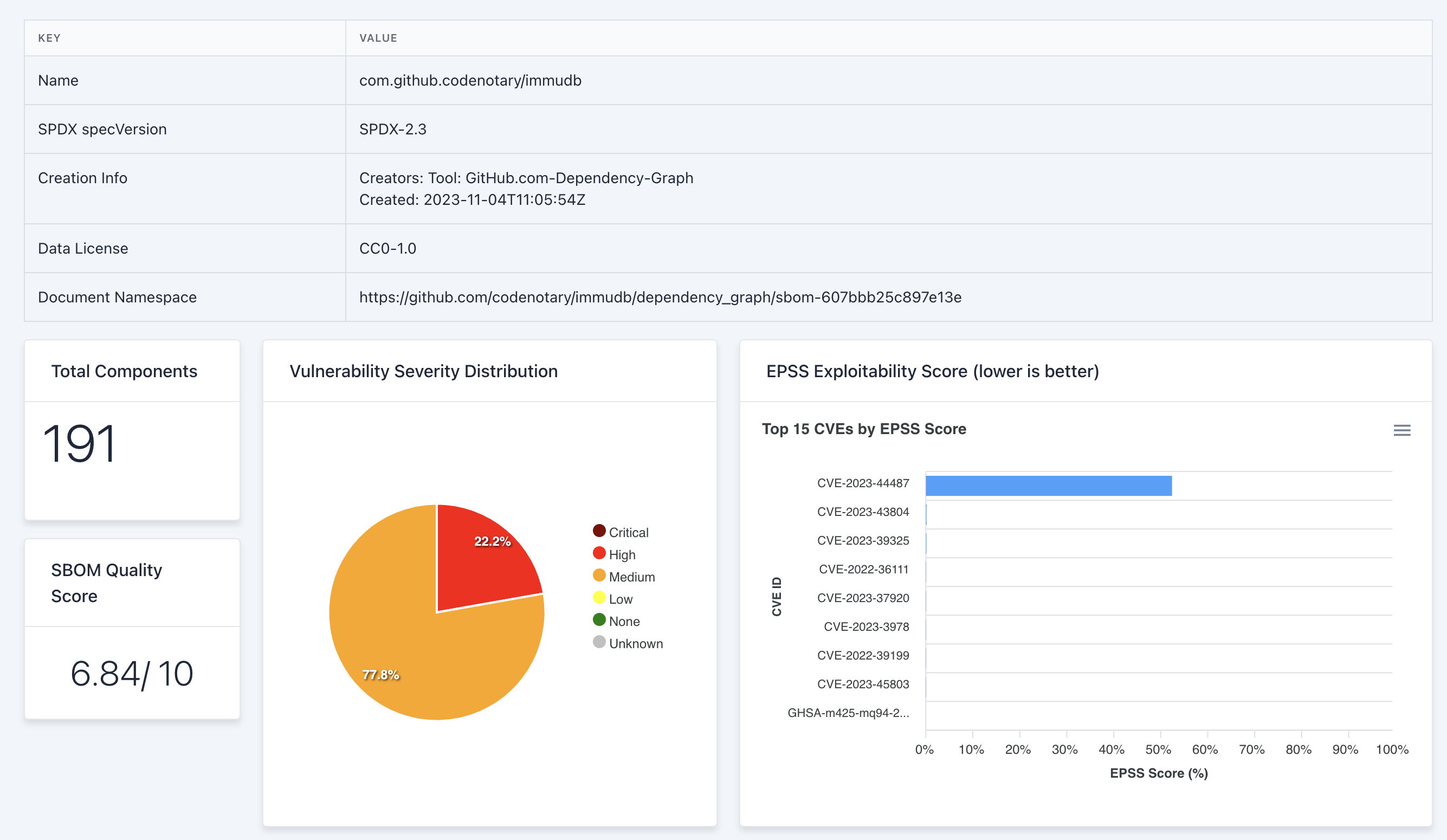
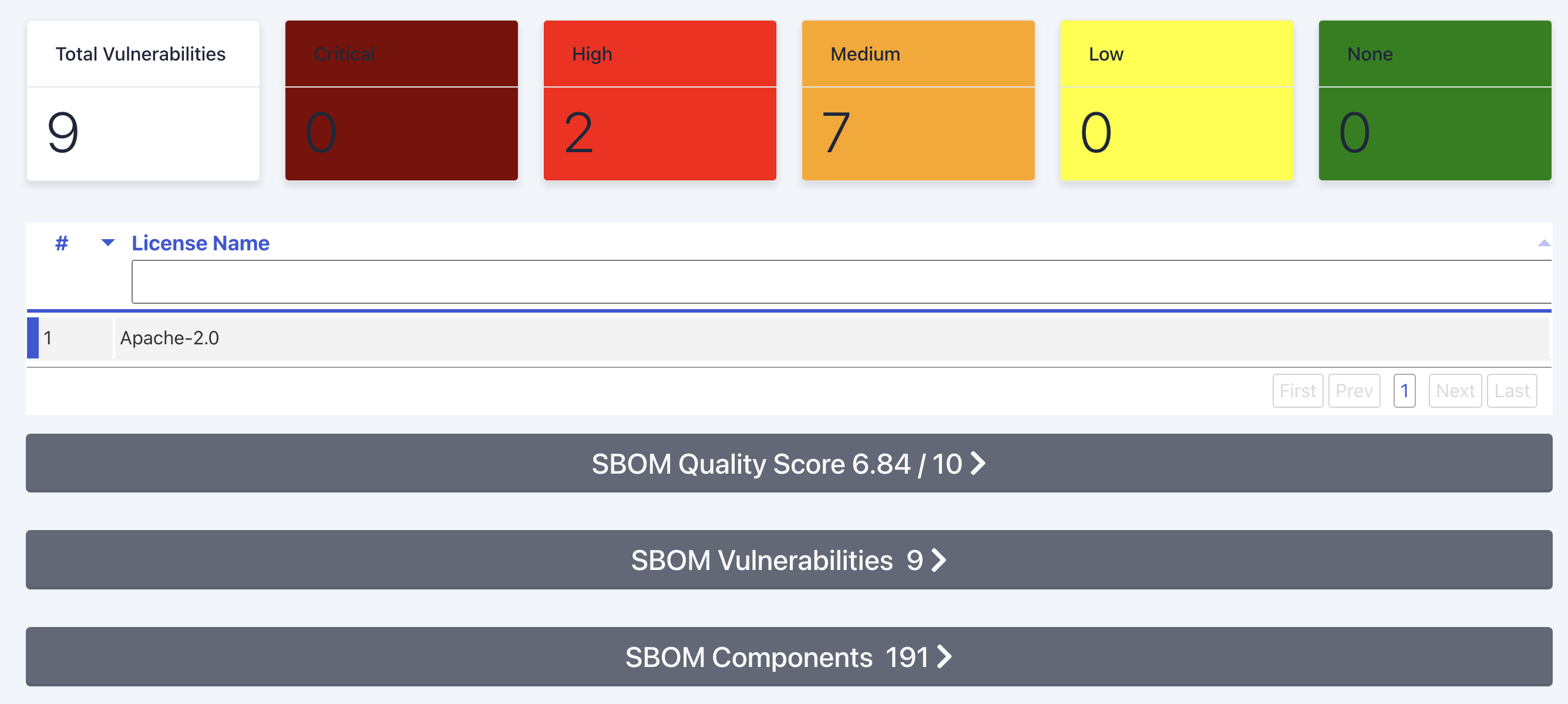
See sbom.sh in Action (Example)
The provided example of an SBOM for a repository offers a detailed insight into the project's components, quality metrics, and vulnerability information. The command used for the example is as follows:curl -sL \ -H "Accept: application/vnd.github+json" \ -H "Authorization: Bearer ghp_xxx" \ -H "X-GitHub-Api-Version: 2022-11-28" \ https://api.github.com/repos/codenotary/immudb/dependency-graph/sbom | jq '.sbom' | curl -X PUT -d @- https://sbom.sh -H "Content-Type: application/json"
Let's break down (some of) the features of this report:
- Identification: Clearly mentions the repository or project.
- Specification Version: Specifies the version of the SPDX specification used for standardization.
- Creation Details: Indicates the tool used for SBOM generation and the timestamp, enhancing traceability.
- Data License: Specifies the data license for the SBOM.
- Access Link: Provides a link for accessing the detailed SBOM.
- Scale: Indicates the project's scale in terms of components.
- Quality Score: Assigns a quality score, offering an overall assessment of the SBOM's reliability.
- Vulnerabilities: Provides an overview of vulnerabilities based on severity.
- Exploitability Score: Assigns a score indicating the potential exploitability of vulnerabilities.
- License Mention: Provides information on the licensing of specific components.
This general SBOM example demonstrates a comprehensive overview of a project, encompassing components, quality metrics, and vulnerability insights. Such an SBOM serves as a valuable resource for developers, aiding in informed decision-making regarding security and quality considerations.
Conclusion
Overseeing dependencies is obviously of utmost importance. GitHub's Dependency Graph streamlines this process by offering a transparent snapshot of dependencies and their interconnections. sbom.sh builds upon it further by providing detailed insights into the quality, vulnerabilities, and exploitability of your project's dependencies. By integrating both GitHub's Dependency Graph and sbom.sh into your workflow, you can truly fortify the security and stability of your projects.
