Jenkins Build Deployment Pipeline: A How To for Ensuring Integrity
In this blog, we will briefly touch on the importance of
- DevOps has strong security
- current hole in DevOps security aka DevSecOps
- Jenkins Automation’s role in the build process
- a technical walkthrough on how to integrate the Codenotary Trustcenter with your Jenkins build deployment pipeline to ensure its integrity
The Weak Link in DevOps Pipelines
DevOps has been widely adopted for many years for its benefits including speeding up the software development process.
However, in the CICD process, there is one significant weak link when it comes to ensuring the integrity of code from development to production. That is, when the build is created, stored on a repository, and then picked up to be deployed into production, no one knows if it has been maliciously edited.
No integrity check was performed on the containers, scripts, clusters, or any of the other build components. It is completely possible that someone could have tampered with the building code and injected it with malware.
Unfortunately, if the code’s integrity was never verified, there is no way to be completely sure what you are deploying is what you built.
Securing DevOps Builds with Codenotary
With CodeNotary, the solution is an easy, single step where you can be 100% sure your code is exactly how you left it. Code integrity is no longer a question with today’s technology. It is now possible to verify the integrity of all of your code at every stage of the build process before you ever deploy anything into production.
Additionally, one of the best things about Codenotary’s robust, multi-layered, security solution is its seamless integration preventing problems from arising and scaling in size later on down the pipeline, creating significant savings in terms of potential patch costs and other associated damages.
By integrating CodeNotary’s distributed ledger technology into your DevOps and Jenkins builds, you now have the ability to keep a 30,000-foot view of all shipped components sent to any customer that scopes down to an infinitely granular level.
Here’s how simple it is to set up Jenkins code build notarization.
Integrating Codenotary Trustcenter into Jenkins Build Deployment Pipeline
In order to maintain an optimal DevSecOps pipeline with your CI/CD build, we have developed an application that can verify the integrity of all your code continuously. The details of how to configure CodeNotary to automatically sign Jenkins’ builds is below. The integration has 3 main steps in what is otherwise can be labeled a 10-step process. The 3 main steps are:
- Configuration at the system level to use vcn credentials system-wide in Jenkins
- Tie vcn credentials in from system configuration to local environment variables per build job and sign assets
- Run vcn verify with asset parameters before deployment
Step 1: System-level configuration
On the Home Screen, locate and click the Credentials link in the sidebar menu to expand the submenu beneath it.
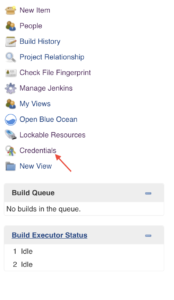
With the submenu opened up, go ahead and select the credentials type, in this case, select System.
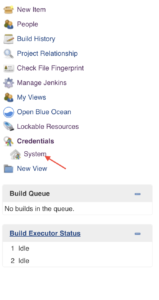
After selecting System, click Add Domain and notice the right-hand display shows ‘Global credentials (unrestricted)’. Click the link.

Create new credentials by selecting the Add Credentials option.

Now that you have the credential creation display opened, you will need to create your credential entries for your vcn keystore password, vcn user account, and vcn password.

Once you have all 3, your list of credentials should look something similar to the one below.

Next, you will need to configure the build job environment for each build job you have. This is relatively simple. All you need to do is to tie the vcn credentials in from the system configuration to the local environment variables by setting the appropriate bindings.
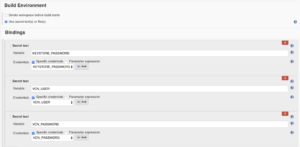
After successfully setting your bindings, you will need to add a building job build step for signing your code with the vcn application. Click on the ‘Add build step’ drop-down and select ‘Execute shell.’
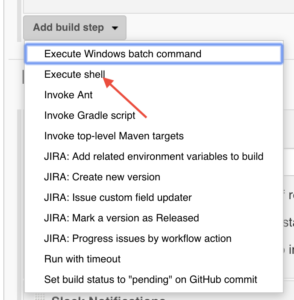
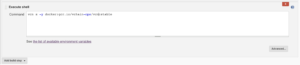
Next, you will need to configure your build step for vcn signing by typing in
vcn s -y docker:gcr.io/vchain-ops/vcn:stable #in the Command field.
Step 3: Before deployment
Lastly, you will need to configure the deployment script for verification by:
- Configure environment variables VCN_USER VCN_PASSWORD KEYSTORE_PASSWORD
- Execute this snippet in the build process
vcn verify docker:gcr.io/vchain-ops/vcn:stable || exit 1
docker-compose up -d
And that’s it. You’re now ready to have vChain CodeNotary provide a perpetually running integrity check into all of your Jenkins build deployment pipeline, as well as ensure you are participating in the latest DevSecOps best practices.