Guardians of Software Security: How SBOMs Impact Your Organization
Introduction
Protecting a software company's reputation is a shared endeavor that spans various teams, each contributing its unique skills and expertise. From conceptualizing, creating, and marketing valuable products to ensuring that they are developed and maintained in compliance with the best practices, every team plays a vital role in averting disruptions for the company and, by extension, its valued customers. Achieving this level of coordination necessitates aligning the goals and strategies across the organization.
SBOM should be at the heart of the reference list for engineering, legal, and security teams, serving as a pivotal tool in their daily processes. By providing this level of detail, SBOMs afford software makers the clarity they need about their product's composition, ensuring they do not unwittingly pass on risks to their users and customers.
While SBOMs are primarily associated with software, it's essential to note that they belong to a broader category of bills of materials (BOMs) applicable to various contexts, including hardware and SaaS products. Within the domain of software, SBOMs are critical for self-attestations, confirming that a software product adheres to secure development best practices. They also come equipped with essential security reports, including vulnerability disclosure reports (VDRs) and vulnerability exploitability exchange (VEX) reports, providing insights into vulnerabilities and future remediation plans.
Navigating the Regulatory Landscape
The regulatory environment for software is undergoing rapid transformation on a global scale. In the United States, adherence to national regulations, such as Executive Order 14028, mandates that software be accompanied by an SBOM. Furthermore, industry-specific requirements, such as the FDA's cybersecurity modernization action plan and NHTSA's guidance for vehicle manufacturers, underscore the importance of SBOMs.
In the European Union, the EU Cyber Resilience Act sets forth requirements that protect both software and hardware with digital components. The convergence of these regulations and the inherent business imperative for SBOM adoption necessitates a concerted effort to align all teams, initiating or continuing the operationalization of SBOM management on a broader scale.
This initiative encompasses various aspects, including the automation of SBOM creation, the maintenance of regular updates, and the integration of SBOMs into comprehensive software composition analysis programs, overseen by open-source program offices (OSPOs).
Aligning SBOM metrics with the specific needs of each persona fosters organization-wide buy-in and encourages the implementation of safeguards.
-
Security Analysts: Chief Information Security Officers (CISOs), security analysts, and their teams require comprehensive knowledge of their organization's software components. SBOMs facilitate the mitigation of cyber threats by helping security teams identify vulnerabilities and efficiently remediate them.
-
Legal Department: Legal teams utilize SBOMs to maintain compliance with software licenses. This is essential for regulatory compliance and streamlining M&A processes, irrespective of whether they are on the buy- or sell-side of a merger or acquisition. Understanding the composition of a company's code is crucial for safeguarding the product, customers, and the business as a whole.
-
Development Teams: Software is an ever-evolving entity. A regularly updated SBOM, integrated into the continuous integration/continuous delivery (CI/CD) process, accelerates development cycles, enhances the ability to catch issues early in the development cycle, and ultimately improves time-to-market, ensuring software projects stay on time and within budget.

Comprehensive Business Improvements
The adoption and effective use of SBOMs have far-reaching impacts, ranging from risk management to operational efficiency. They are instrumental in mitigating cyber threats and enhancing operational efficiency. Automated SBOMs, when created with the right tools, reduce the time developers spend on rectifying non-compliant open-source code, thereby freeing up valuable time for the creation of unique and distinctive products for your marketplace.
Furthermore, SBOMs serve to strengthen relationships with the entire supply chain, benefitting both partners and customers. By disclosing the composition of your applications and the associated risks, all parties involved can be assured that you are committed to following best practices.
Discover SBOM.sh for Seamless SBOM Management
How are you utilizing SBOMs to bolster your security posture and cultivate stronger relationships within your supply chain?
To streamline the sharing and retrieval of SBOMs, sbom.sh offers a pioneering solution. Developers, teams, and organizations can effortlessly upload local SBOM JSON files and receive a unique URL. This URL allows convenient access to SBOM data, enabling retrieval through curl commands or direct web browser access. sbom.sh simplifies SBOM management, ensuring that your software remains secure, compliant, and in alignment with best practices.
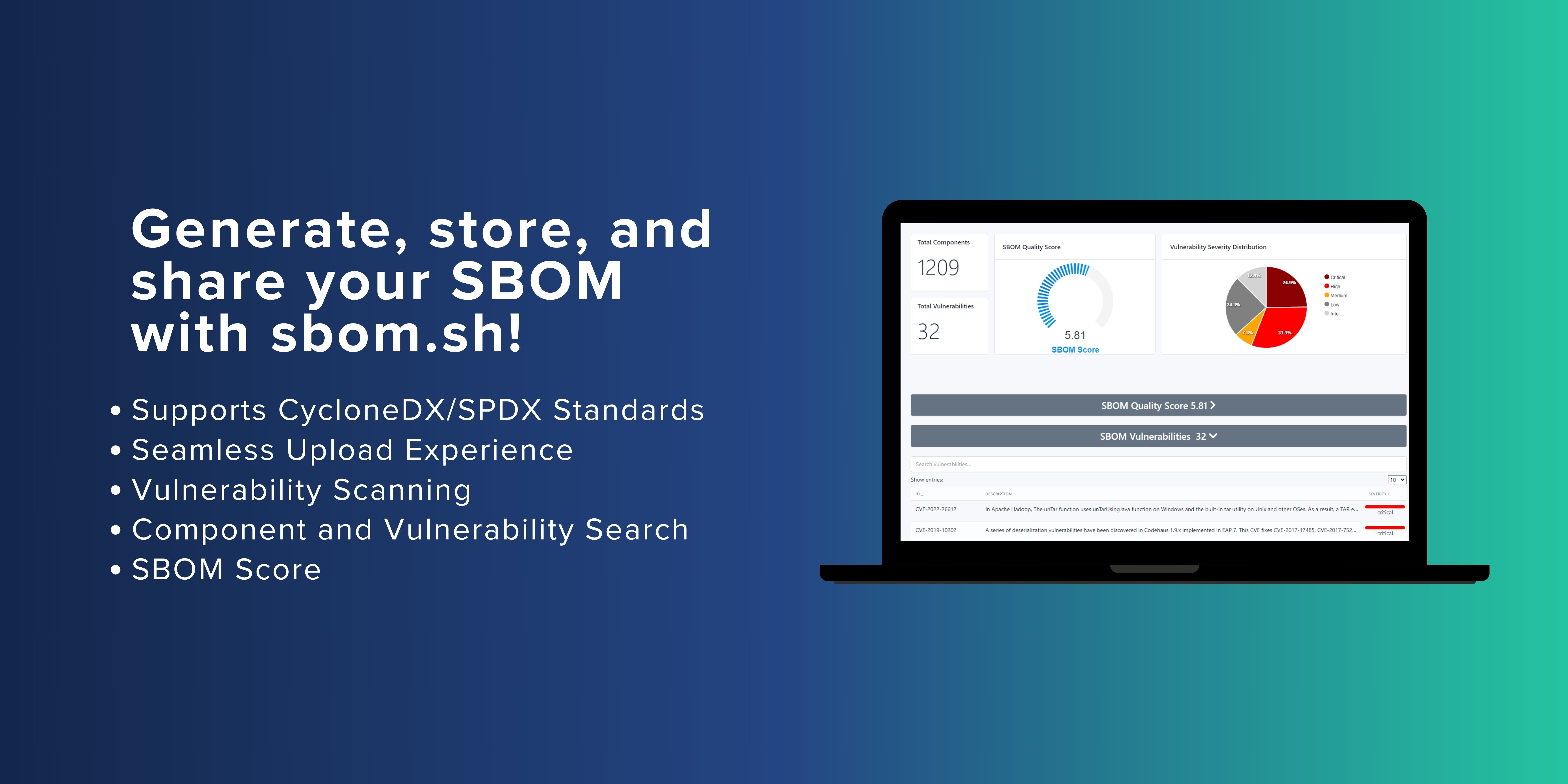
Visit sbom.sh today to up your SBOM management game. Make SBOMs an integral part of your software security posture and strengthen the relationships within your supply chain.
