GitHub Blunder: Accidental Exposure of 38TB of Sensitive Data
Introduction
Recently, a Microsoft employee found themselves at the center of a significant data security incident, inadvertently exposing a staggering 38 terabytes of sensitive data on GitHub. This mishap has raised concerns about the security measures in place at one of the world's leading technology companies. However, amid the discussion of this unfortunate event, we also have an opportunity to introduce a promising solution: sbom.sh, but we'll get into that a little later.
.jpg?width=6912&height=3456&name=Brown%20Peach%20Illustrative%20GreetingsSlogans%20Banner%20Landscape%20(3).jpg)
The GitHub Blunder
The incident came to light through the diligent efforts of Wiz security researchers who discovered the exposed data. The mishap occurred while the Microsoft employee was publishing a bucket of open-source AI training data on GitHub. Instead of safeguarding this treasure trove of information, they unintentionally made it accessible to the world.
The Data Exposed
What made this incident particularly alarming was the nature of the exposed data. Wiz researchers discovered that the leaky account contained private keys, passwords, and over 30,000 internal Microsoft Teams messages. Additionally, sensitive data from personal computer backups of two former employees, including passwords to Microsoft services and secret keys, was also at risk.
Introducing sbom.sh
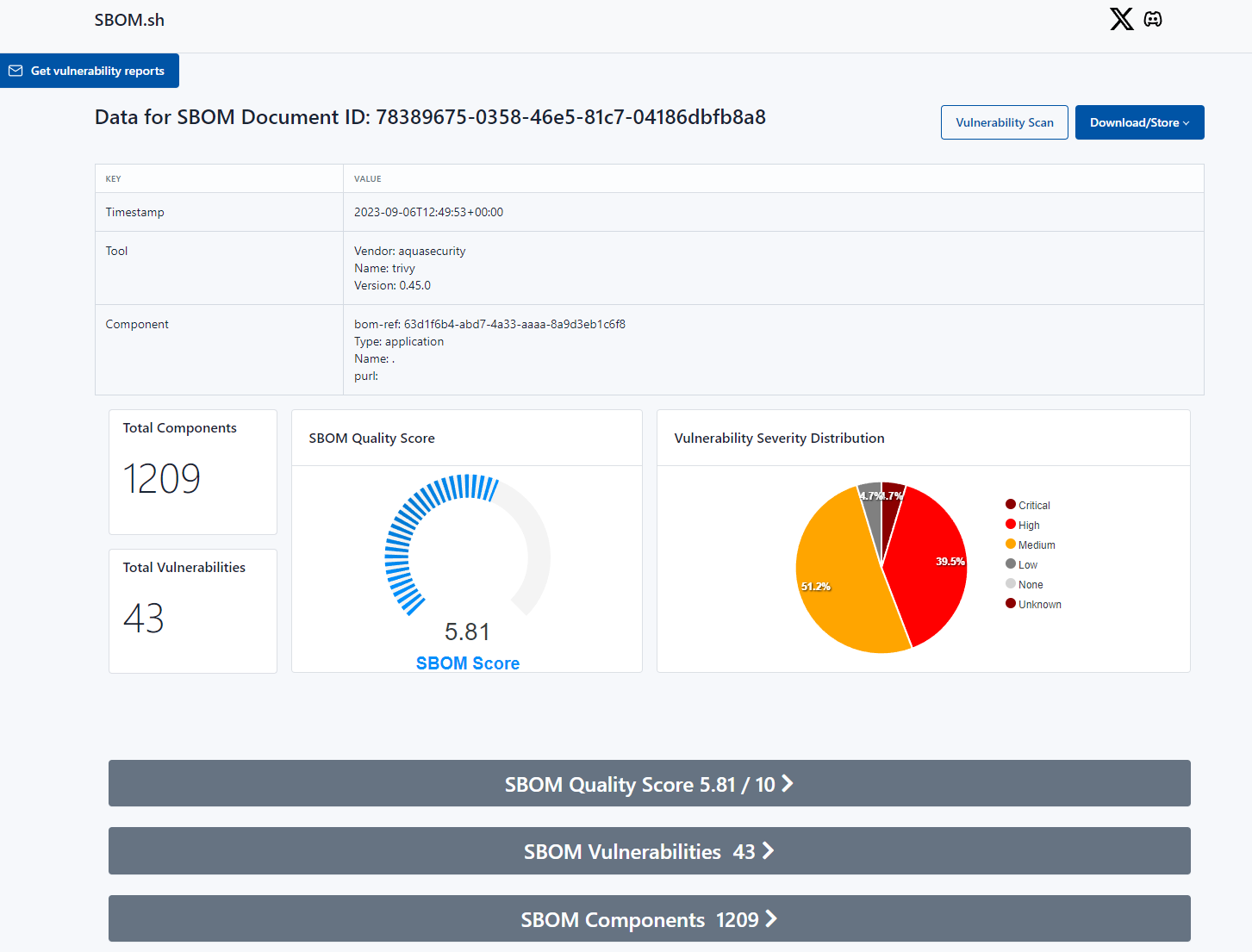
Amid concerns about data security and sharing, sbom.sh emerges as a solution. sbom.sh is a service designed to streamline the sharing and retrieval of SBOM (Software Bill of Materials) data, which is crucial for understanding the composition of software components and dependencies.
sbom.sh allows developers, teams, and organizations to effortlessly upload local SBOM JSON files and receive a unique URL. This URL can be accessed anytime, either through curl commands or directly from a web browser, to retrieve the SBOM data. By using sbom.sh, organizations can ensure the transparent sharing and access to essential software information, reducing the risk of mishaps like the GitHub exposure incident.
Microsoft's Response and Learning from Mistakes
When confronted with the gravity of the situation, Microsoft's response might surprise some. In their official statement, they downplayed the incident, characterizing it as an opportunity to share knowledge. They emphasized that no customer data was exposed, and no other internal services were compromised. According to the Microsoft Security Response Center team, "No customer action is required in response to this issue."
Microsoft acknowledged that there was room for improvement. In their statement, they expressed their commitment to enhancing their detection and scanning tools to proactively identify cases of over-provisioned SAS URLs and enhance their secure-by-default approach.
Conclusion
The accidental exposure of 38 terabytes of sensitive data on GitHub, originating from a Microsoft employee, serves as a stark reminder that even industry giants can make critical mistakes in data security. It's a wake-up call for organizations worldwide to continuously prioritize cybersecurity and remain vigilant in the face of evolving threats. Microsoft's response to this incident reflects the need for transparency, learning from mistakes, and reinforcing data protection measures.
In the realm of data security and the sharing of sensitive software information, sbom.sh is a promising solution. It empowers developers, teams, and organizations to securely share and access SBOM data, reducing the risk of data exposure incidents like the one at Microsoft. As the tech community learns from such incidents, solutions like SBOM.sh become increasingly vital for protecting the integrity and security of our data and software assets.