Enhancing Cybersecurity through SBOMs with sbom.sh
Introduction
Recent cyber incidents, such as the SolarWinds breach, Microsoft Exchange vulnerabilities, and the Colonial Pipeline attack, have highlighted the vulnerabilities faced by both public and private sector organizations. To address these challenges, the U.S. government has taken significant steps to improve the nation's cybersecurity posture, including the revision of the Federal Acquisition Regulation (FAR) to foster greater information sharing about cyber threats and incidents. sbom.sh lets you effortlessly create and share an SBOM in one step, and is poised to play a pivotal role in this effort.

Executive Order 14028: A Catalyst for Change
Executive Order 14028, signed by the President on May 12, 2021, and published in the Federal Register at 86 FR 26633 on May 17, 2021, serves as a cornerstone for enhancing the nation's cybersecurity. One of its key objectives is to bolster the protection of government networks and foster increased information sharing between government entities and IT and OT service providers. To achieve these goals, the Department of Defense (DoD), the General Services Administration (GSA), and NASA are proposing revisions to the FAR.
The Proposed Changes
The proposed FAR changes align with the recommendations outlined in E.O. 14028, as well as those from the Office of Management and Budget (OMB) and the Cybersecurity and Infrastructure Security Agency (CISA). These changes aim to standardize contract requirements for cybersecurity and hold accountable those who jeopardize U.S. information or systems. Here are some key highlights of the proposed changes:
-
Definition Update: The term "information and communication technology" (ICT) replaces "information technology." This update expands the scope to include telecommunications services, electronic media, Internet of Things (IoT) devices, and operational technology. Additionally, the term "software" is revised to "computer software" to align with previously defined terminology.
-
New Definitions: The proposed FAR changes introduce definitions for IoT devices, operational technology, telecommunications equipment, and telecommunications services. These definitions help standardize the understanding of key components in the cybersecurity landscape.
-
IPv6 Implementation: The revisions include guidance on transitioning to Internet Protocol Version 6 (IPv6) as outlined in OMB Memorandum M–21–07, further enhancing network security.
-
Incident Reporting: The FAR updates include provisions for reporting security incidents and requests for information or access, ensuring swift responses to potential threats.
-
Contractual Changes: Several FAR clauses, such as 52.239–ZZ, Incident and Threat Reporting and Incident Response Requirements for Products or Services Containing Information and Communications Technology, have been added to address security incident reporting, supporting incident response, and more.

Software Bills of Materials (SBOMs): A Game-Changing Requirement
One of the most significant additions proposed in the FAR changes is the requirement for contractors to develop and maintain a Software Bill of Materials (SBOM) for any software used in the performance of a contract. This requirement, irrespective of whether a security incident occurs, is a critical step in enhancing cybersecurity. SBOMs, as outlined in section 10(j) of E.O. 14028, are comprehensive lists of software components used in a system or application.
SBOMs are invaluable for incident response as they enable quick identification of known vulnerabilities. They provide essential insights into the software supply chain, allowing organizations to assess and mitigate risks effectively. To support this effort, sbom.sh offers an easy way to create and share SBOMs, ensuring compliance with the new FAR requirements.
Anticipating Challenges and Seeking Solutions
As we move forward with these proposed changes, it's important to consider potential challenges and solutions:
-
Collecting SBOMs: How should SBOMs be collected from contractors, and what protections are necessary for the information they contain?
-
Scope of Requirement: What is the appropriate scope of the SBOM requirement to ensure security while not imposing undue burdens on contractors?
-
Challenges in Development: What challenges will contractors face in developing SBOMs, especially regarding legacy software and software resellers?
-
Updating SBOMs: How should organizations evaluate when an SBOM must be updated based on changes in new builds or major releases?
-
Monitoring SBOMs: What is the right balance between government and contractors when monitoring SBOMs for embedded software vulnerabilities?
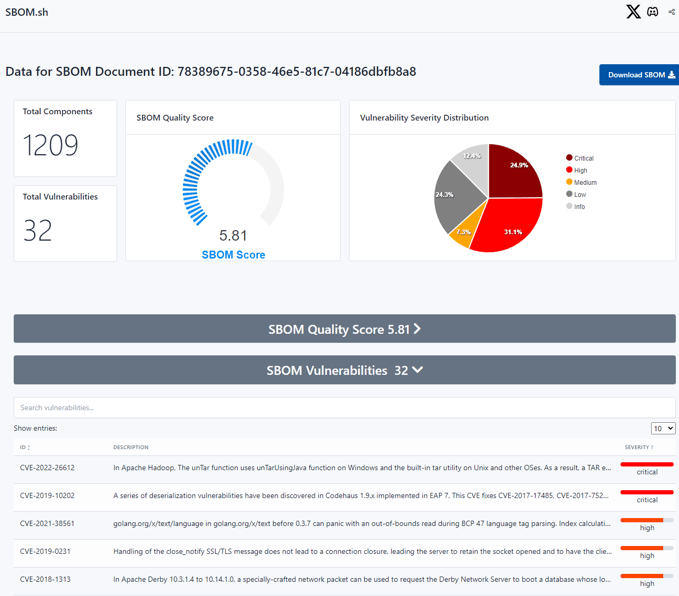
Conclusion
The proposed FAR changes, driven by E.O. 14028, are a significant leap forward in strengthening the cybersecurity posture of the United States. As cybersecurity threats continue to evolve, it is imperative that government agencies and contractors work together to enhance information sharing, incident response, and vulnerability management. With its user-friendly SBOM creation and sharing capabilities, sbom.sh is well-positioned to support organizations in complying with these new requirements and ensuring a safer digital landscape for all.
