Dirty Pipe, a new vulnerability
On March 7th a new bad vulnerability was publicly disclosed, affecting a recent Linux kernel. It is particularly bad because it allows any local user to overwrite any file, even those that are supposed to be read-only for that user.
Dirty Pipe

This can lead to a very wide number of different attacks, and it is so very important to upgrade the kernel to a safe version as soon as possible.
Since the vulnerability is centered on “pipes”, they used the name “dirty pipe” to describe it. The actual CVE for this is CVE-2022-0847.
The discoverer wrote a very good article on it, and you can find it here: https://dirtypipe.cm4all.com/
Am I affected by this?
Since the vulnerability is affecting some recent kernels, but not all, it is important to understand if a machine is impacted or not.
The vulnerability was published, on the kernel security mailing list, on the 20th of February, so a fix was prepared and some distributors have already incorporated it in their kernel.
Kernels older than 5.8 or more recent than 5.16.11 are (or should be) safe, but everything in between must be checked.
Ubuntu and Debian (two of the most widely used distributions) haven’t yet shipped a kernel package for their vulnerable systems.
A Proof of Concept (PoC) code is presented in the article, but it requires some additional steps that not everyone is familiar with. So, starting from that code, I’ve prepared a quick binary that can be used to check if the system you are working with is vulnerable.
You can find it here: https://github.com/SimoneLazzaris/ditty
Just download the “ditty” binary from https://github.com/SimoneLazzaris/ditty/releases and launch it from a command prompt.
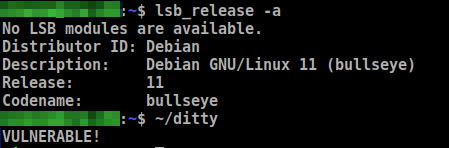
If the system you are on is vulnerable, you’ll have to update it as soon as possible. If a binary is not ready yet, you may need to manually compile a newer version of the kernel or tighten up the perimetral security so that no unwanted user may access your system.
