Binary Security: Using BLint for Effortless Generation of SBOMs
As developers and DevOps professionals, we understand the importance of software security. One crucial aspect of securing the software supply chain is maintaining a Software Bill of Materials (SBOM). An SBOM provides a detailed inventory of all the components used to build your software, including libraries and dependencies. This transparency allows for quicker identification and remediation of vulnerabilities.
BLint, a project by the OWASP Dependency Scanning (dep-scan) initiative, offers a valuable tool for generating SBOMs alongside its core functionality of analyzing binary security properties. This blog post dives into how BLint simplifies SBOM generation, making it easier to integrate security best practices into your development workflow.
https://github.com/owasp-dep-scan/blint
BLint: Beyond Binary Linting
BLint goes beyond just checking the security posture of your executables. Since version 2, it has also transformed into a powerful SBOM generator. This functionality empowers developers and DevOps teams to streamline SBOM creation without introducing complex new tools.
.png?width=1200&height=630&name=CN-Assets%20(40).png)
Generating SBOMs with BLint
Utilizing BLint for SBOM generation is straightforward. Here's a basic command-line example:
blint sbom -i path/to/your/binary -o path/to/your/sbom.json
This command instructs BLint to analyze the binary located at "path/to/your/binary" and generate an SBOM in JSON format. The SBOM is then saved to the specified location, "path/to/your/sbom.json". BLint also supports other output formats like SPDX and CycloneDX, offering flexibility based on your preference.
BLint can not only process individual binaries but can also analyze entire directories containing executables. For instance, the following command processes all executables within the "bin" directory and creates individual SBOMs in JSON format:
blint sbom -i path/to/your/binary-directory -o path/to/your/sbom.json --deepHere, BLint analyzes each binary within the "bin" directory and generates a corresponding SBOM saved in the "sbom_output_directory".
Uploading SBOMs to sbom.sh
Once you've generated your SBOM using BLint, you can upload it to a public repository like sbom.sh. Or you can skip the step of storing the file and directly sending to https://sbom.sh for centralized management and sharing. The curl command-line utility provides a convenient way to upload your SBOM to sbom.sh. Here's an example to use blint and curl in one line:
blint sbom -i /usr/sbin/sshd -o --stdout | curl -T - https://sbom.sh
This command uses curl to perform a PUT request to the sbom.sh API, the - argument is the placeholder for the standard out of the command sending into the pipe (blint in this example).
If you are a fan of step by step, you can execute the commands sequentially for generating the SBOM file using BLint and managing the SBOMs using SBOM.sh, enhancing the overall security posture of your software development lifecycle.
Let's take the sshd binary as an example:
blint sbom -i /usr/sbin/sshd -o /tmp/sshd_sbom.json
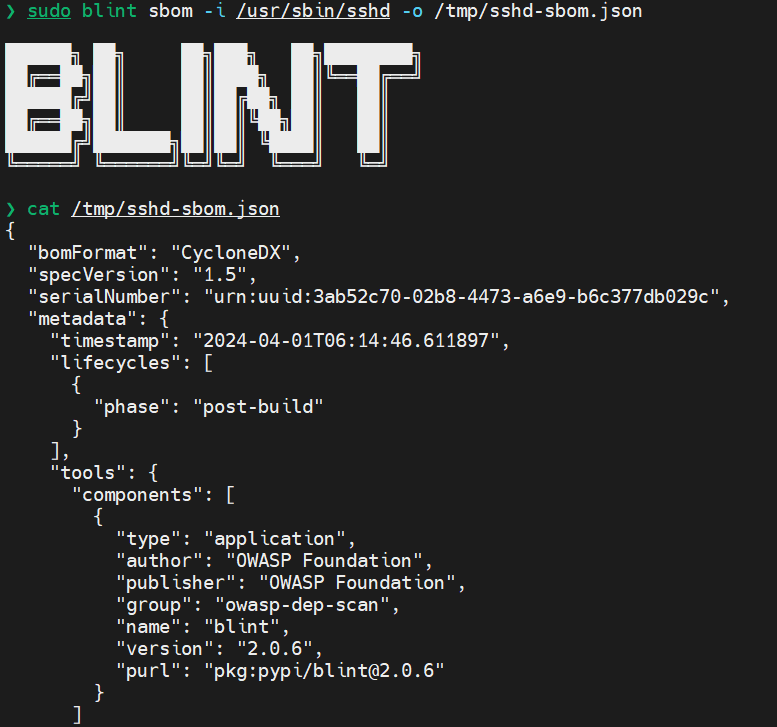
and send it to https://sbom.sh:
curl -T /tmp/sshd_sbom.json https://sbom.sh
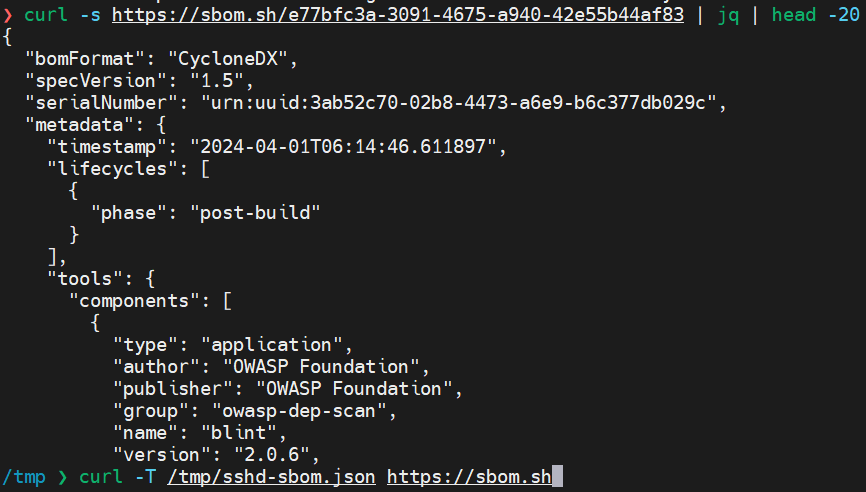
Now you can use your browser or curl to access the sbom using the returned unique URL
.png?width=1200&height=630&name=CN-Assets%20(39).png)
Incorporating BLint into Your Workflow
Integrating BLint into your existing CI/CD pipeline is an excellent way to automate SBOM generation. This ensures consistent SBOM creation for every build, fostering a more secure development environment. The BLint project repository provides comprehensive documentation to guide you through the integration process.
BLint empowers developers and DevOps teams to generate SBOMs effortlessly. With its user-friendly interface and powerful capabilities, BLint simplifies security practices and streamlines SBOM management, ultimately contributing to a more secure software supply chain.
Note: Remember to replace placeholders like "path/to/your/binary" and "path/to/your/sbom.json" with the actual file paths on your system.